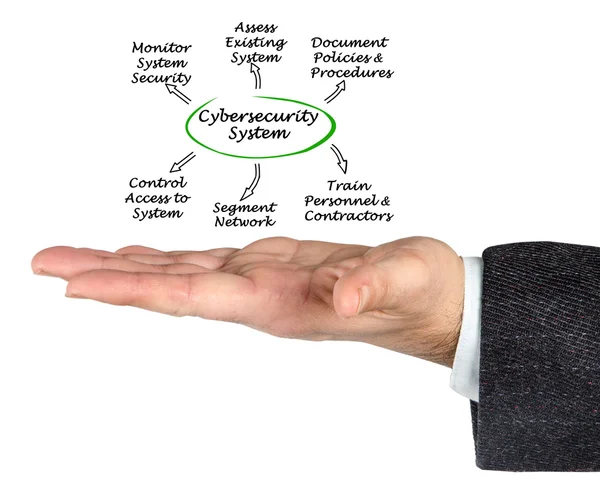
Stock image Access Policies page 2
Cyber Security With Firewall. Digital Technology Protection Data Concept. 3d Perspective Vector Illustration.
Vector, 3.95MB, 12500 × 7292 eps

Data Compliance Cartoon Banner Template. Vector Illustration Of Laptop, Shield Lock, Credit Card, Folder With Papers, Brick Wall, Cloud And Checkmark Icons. Symbols Of Information Security Protection
Vector, 1.35MB, 6000 × 3000 eps

Inspiration Showing Sign Data Governance, Concept Meaning General Management Of Key Data Resources In A Company
Image, 5.37MB, 9000 × 4005 jpg

Modern, Vibrant Photo Illustrating The Concept Of Cybersecurity, Password Or Computer Hacking
Image, 0MB, 4240 × 2832 jpg

Implement SSO Solutions To Enable Users To Log In Once And Gain Access To Multiple Financial Services Without Needing To Re-authenticate
Image, 0.8MB, 2600 × 1728 jpg

Understanding The Diversity Of Cloud Users - Demographics And Behavior
Image, 1.73MB, 5851 × 3000 jpg

Compliance Settings Help Organizations Meet Industry Standards And Regulatory Requirements
Image, 9.71MB, 7212 × 4000 jpg

Continuous Monitoring Of Cloud Environments Detects And Responds To Security Incidents In Real-time, Mitigating Potential Threats
Image, 1.13MB, 6132 × 3000 jpg

Obust Access Control Mechanisms Enforce Least Privilege Principles, Limiting Access To Data And Resources Based On User Roles And Permissions
Image, 10.95MB, 7212 × 4000 jpg

X Has New Rules That Officially Allow Porn Now. Jakarta, 26 June 2024.
Image, 1.1MB, 4220 × 2374 jpg

Luxury Red Inscription Sanctions On Grey Podium With Boxes, Soft Light, Front View Smooth Background, 3d Rendering
Image, 12.83MB, 8000 × 5000 jpg
Previous << Page 2 >> Next