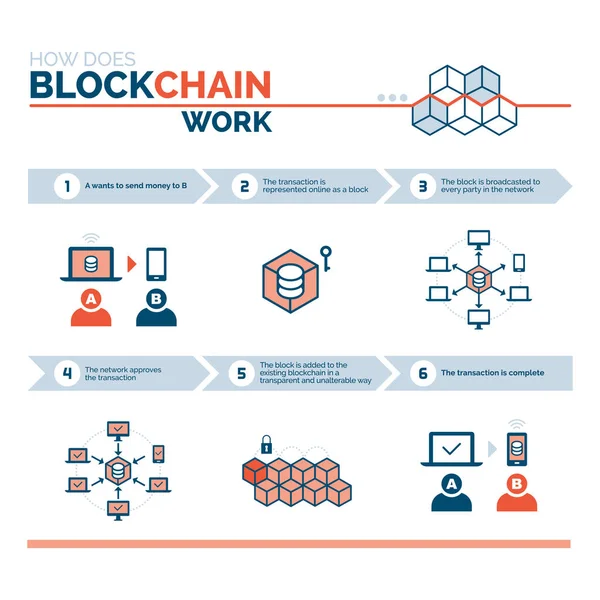
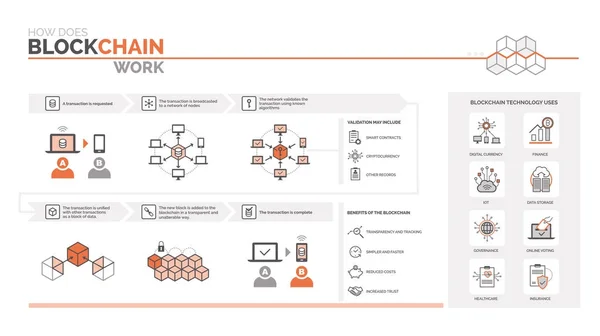
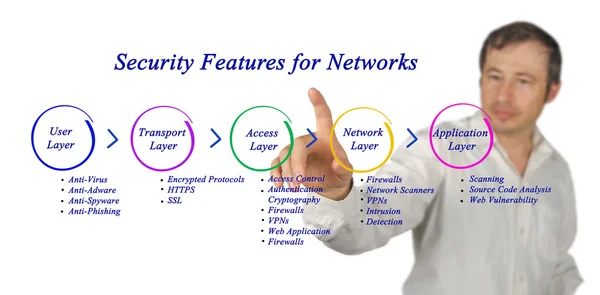
Stock image Authentication Process

Users Enhance Cyber Protection By Typing Secure Login Credentials, Incorporating Two-factor Authentication For Additional Layer Of Safety When Accessing Secured Login Form, Ensuring Protected Access
Image, 4.81MB, 6048 × 4024 jpg

Autentication Login Form Concept With Hands On A Laptop. Seamless Security Integration For A Clean And Functional Tech Visual
Image, 6.15MB, 6016 × 4016 jpg

A Businessman's Finger Tapping Or Activating A Virtual Digital Padlock For Safe Online Account Access, After Entering His Username And Password. Cybersecurity.
Image, 3.68MB, 9308 × 4042 jpg

Word Writing Text Managed Services. Business Concept For Company That Remotely Analysisages Customer S Is IT Infrastructure.
Image, 3.46MB, 6000 × 4006 jpg

Vector Authentication Infographic Template. Include Fingerprint Recognotion, Face Authentication, Face Detection, Handwriting Identification And Others. Icons In Different Colors.
Vector, 3.78MB, 7000 × 4667 eps

Conceptual Hand Writing Showing Online Registration. Business Photo Text Process To Subscribe To Join An Event Club Via Internet.
Image, 6.64MB, 6000 × 3698 jpg
?oncept Process Automation On The Gears. Gold And Silver Gear Weel Background Illustration 3d Illustration.
Image, 2.95MB, 3840 × 2160 jpg

Vector Authentication Infographic Template. Include Fingerprint Recognotion, Face Authentication, Face Detection, Handwriting Identification And Others. Icons In Different Colors.
Vector, 3.21MB, 7000 × 4667 eps

Two-factor Authentication (2FA) And Fingerprint Touch Identification Security Concept. User With Digital Tablet And Smart Phone And Two-factor Authentication Security Process, Flatlay Design.
Image, 13.98MB, 5616 × 3744 jpg

Two-factor Authentication (2FA) And Fingerprint Touch Identification Security Concept. User With Digital Tablet And Smart Phone And Two-factor Authentication Security Process, Flatlay Design.
Image, 14.27MB, 5616 × 3744 jpg

Two-factor Authentication (2FA) And Face Identification Security Concept. User With Digital Tablet And Smart Phone And Two-factor Authentication Security Process, Flatlay Design.
Image, 14.29MB, 5616 × 3744 jpg
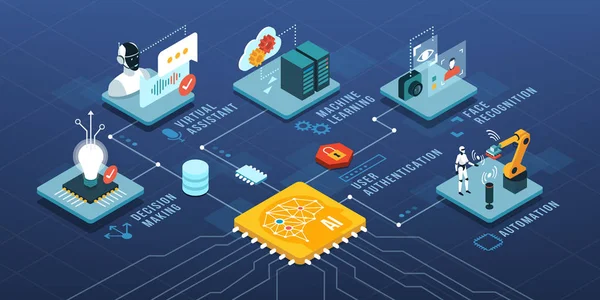
Artificial Intelligence, Automation And Machine Learning Isometric Infographic With Text
Vector, 10.33MB, 7000 × 3500 eps

Two-factor Authentication (2FA) And Face Identification Security Concept. User With Digital Tablet And Smart Phone And Two-factor Authentication Security Process, Flatlay Design.
Image, 13.99MB, 5616 × 3744 jpg

Application Development Vector Infographic Template. Business Presentation Design Elements. Data Visualization With Four Steps And Options. Process Timeline Chart. Workflow Layout With Linear Icons
Vector, 1.2MB, 10060 × 3000 eps

Innovative Smartphone With AI Applications Vector Infographic: Virtual Assistant, Performance Optimization, User Authentication, Productivity, Decision Making
Vector, 16.65MB, 7000 × 3500 eps

Smartphone With Locked Access To Information. Notification With Authorization Form On Screen. Notification With A Password. Vector Illustration In Flat Style.
Vector, 1.12MB, 4134 × 4134 eps
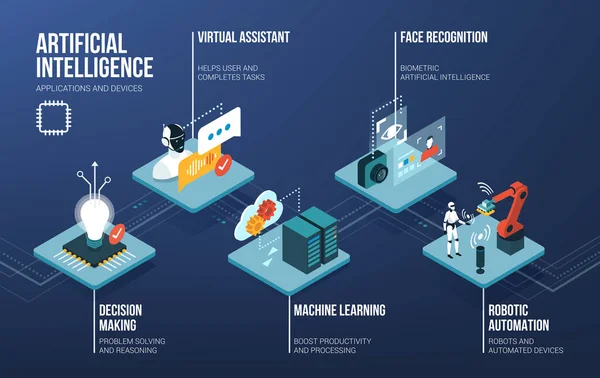
Artificial Intelligence, Automation And Machine Learning Isometric Infographic With Text
Vector, 9.72MB, 7000 × 4417 eps

Artificial Intelligence Applications, Smart Devices, Robots And Automation: Network Of Isometric Objects Connecting Together
Vector, 11.05MB, 7000 × 3500 eps

Text Sign Showing Managed Services. Conceptual Photo Company That Remotely Analysisages Customer S Is IT Infrastructure.
Image, 3.85MB, 6000 × 4005 jpg

Software Development Vector Infographic Template. Business Presentation Design Elements. Data Visualization With Four Steps And Options. Process Timeline Chart. Workflow Layout With Linear Icons
Vector, 0.99MB, 6879 × 3000 eps

Enterprise Client Is Activating Three Managed Services Icons On A Virtual Control Interface With Hexagonal Buttons. Business And Information Technology Concept For Outside IT Management. Copy Space.
Image, 0MB, 7680 × 3840 jpg

Notification With Lock And Password On Screen Laptop. Private Access To Documents. Window With User Authorization. Vector Illustration In Flat Style.
Vector, 1.13MB, 4134 × 4134 eps

Login Authorization, Password, Personal Account Access, System Update, Vector Isometric Illustration.
Vector, 5.09MB, 6299 × 3643 eps

Login Concept With Security Username And Password People Standing Access With Isometric Flat Style Vector
Vector, 4.43MB, 6000 × 6000 eps
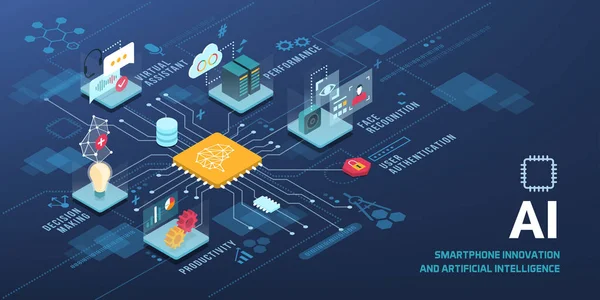
AI Technology Innovative Applications Vector Infographic: Virtual Assistant, Performance Optimization, User Authentication, Productivity, Decision Making
Vector, 16.52MB, 7000 × 3500 eps

Fingerprint Access, Business Security Concept, 3d Isometric Vector Illustration On Ultraviolet Background
Vector, 0.45MB, 5000 × 5000 eps

Login Form Page With Green Tick Icon, Username And Password. Window Browser With User Authorization. Registration Form. Vector Illustration In Flat Style.
Vector, 1.11MB, 4134 × 4134 eps

Two-factor Authentication (2FA) And Verification Security Concept. User With Digital Tablet And Smart Phone And Two-factor Authentication Security Process. Verify Code On Smart Phone, Flatlay Design.
Image, 14.35MB, 5616 × 3744 jpg

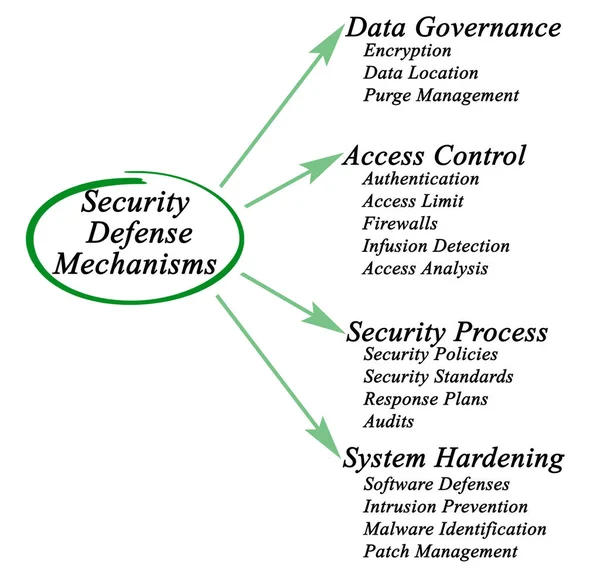
Word Writing Text Data Governance. Business Photo Showcasing General Management Of Key Data Resources In A Company
Image, 1.85MB, 4918 × 3011 jpg

Notification With Lock And Password On Screen Laptop. Private Access To Documents. Window With User Authorization. Vector Illustration In Flat Style.
Vector, 1.12MB, 4134 × 4134 eps

Data Protection. Desktop Pc With Authorization Form On Screen, Personal Data Protection. Isometric Hands On The Keyboard. System Of Authentication. 3d Isometric Design. Vector Illustration.
Vector, 5.19MB, 5048 × 4952 eps

Two-factor Authentication (2FA) And Verification Security Concept. User With Digital Tablet And Smart Phone And Two-factor Authentication Security Process. Verify Code On Smart Phone, Flatlay Design.
Image, 14.08MB, 5616 × 3744 jpg

Notification With Authorization Form On Screen Laptop. Password Login. Username Form. Registration Form. Vector Illustration In Flat Style.
Vector, 1.11MB, 4134 × 4134 eps

Artificial Intelligence Applications, Smart Devices, Robots And Automation: Network Of Isometric Objects Connecting Together
Vector, 6.12MB, 7000 × 3500 eps

Inspiration Showing Sign Data Governance, Concept Meaning General Management Of Key Data Resources In A Company
Image, 5.37MB, 9000 × 4005 jpg

Two-factor Authentication Verification Isolated Cartoon Vector Illustrations. Two-factor Authentication Process, Digital Data Loss Prevention, IT Technology, Set 2FA Vector Cartoon.
Vector, 5.82MB, 5209 × 5210 eps
Page 1 >> Next