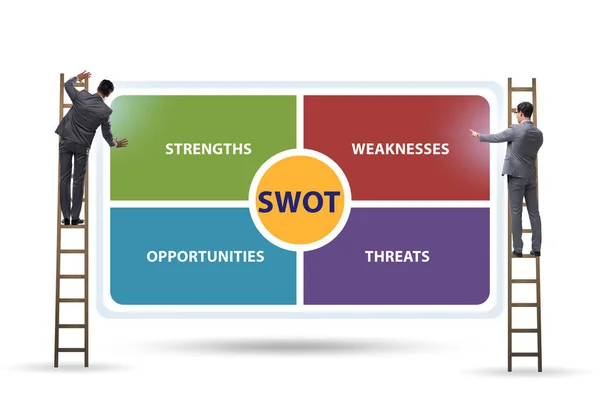
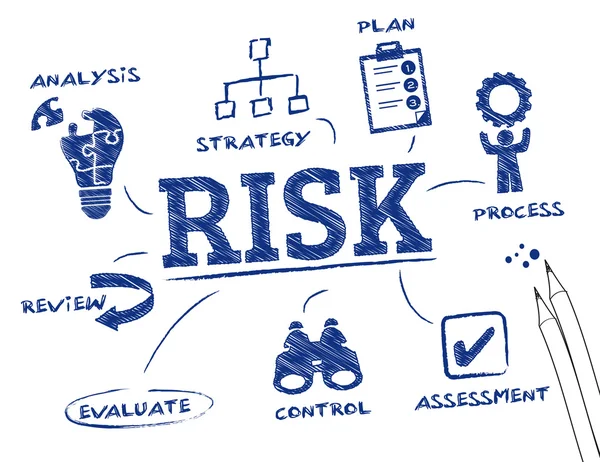
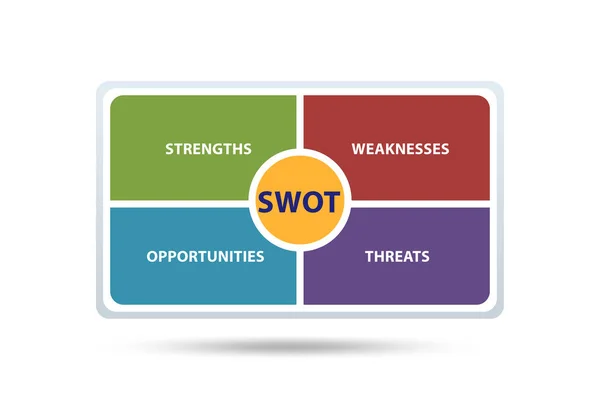
Stock image Bedrohungslage

Handwriting Text Threat Assessment. Concept Meaning Determining The Seriousness Of A Potential Threat.
Image, 3.03MB, 6000 × 3588 jpg

Conceptual Display Threat Assessment. Business Showcase Determining The Seriousness Of A Potential Threat Typing Certification Document Concept, Retyping Old Data Files
Image, 4.25MB, 6000 × 4005 jpg

Perform A Threat Assessment Blue Gradient Concept Icon. Security Standards, Vulnerability. Round Shape Line Illustration. Abstract Idea. Graphic Design. Easy To Use In Infographic, Presentation
Vector, 0.54MB, 5000 × 5000 eps

Perform A Threat Assessment Soft Blue Concept Icon. Security Standards, Vulnerability. Round Shape Line Illustration. Abstract Idea. Graphic Design. Easy To Use In Infographic, Presentation
Vector, 0.52MB, 5000 × 5000 eps

Types Of Security Practices Blue Onboarding Mobile App Screen. Walkthrough 5 Steps Editable Graphic Instructions With Linear Concepts. UI, UX, GUI Template. Montserrat SemiBold, Regular Fonts Used
Vector, 2.64MB, 7000 × 2850 eps

Perform A Threat Assessment Multi Color Concept Icon. Security Standards, Vulnerability. Round Shape Line Illustration. Abstract Idea. Graphic Design. Easy To Use In Infographic, Presentation
Vector, 0.52MB, 5000 × 5000 eps

Application Security Practices Rectangle Infographic Vector. Threat Management, Access Control. Data Visualization With 5 Steps. Editable Rectangular Options Chart. Lato-Bold, Regular Fonts Used
Vector, 1.43MB, 6000 × 3154 eps

Binary Code And Skull With Crossbones Image Over Digital Background. Technology, Cybersecurity, Hacking, Malware, Data Breach, Threat
Image, 0.73MB, 4096 × 2160 jpg

Application Security Practice Types Infographic Vertical Sequence. Threat Management. Visualization Infochart With 5 Steps. Circles Workflow. Montserrat SemiBold, Lato Regular Fonts Used
Vector, 1.41MB, 3500 × 5928 eps

Businessman With Magnifying Glass Analyze Question Marks, Problem Analysis Or Problem Management, Investigate For Root Cause Or Incident, Finding Solution Or Discover Threat Or Uncertain
Vector, 5.25MB, 3000 × 3000 eps

Application Security Best Practices Onboarding Mobile App Screen. Walkthrough 5 Steps Editable Graphic Instructions With Linear Concepts. UI, UX, GUI Template. Montserrat SemiBold, Regular Fonts Used
Vector, 1.57MB, 7000 × 2850 eps

Software Security Practice Types Circular Diagram Infographic. Threat Assessment. Data Visualization With 5 Options. Hierarchy Chart Round. Montserrat SemiBold, Lato Regular Fonts Used
Vector, 1.42MB, 5000 × 5000 eps

Male Corporate Auditor Pushing IT Security Assessment On A Virtual Control Screen. Information Technology Concept For Computer Security Auditing Process And Security Management. Close Up Torso Shot.
Image, 0MB, 7680 × 3840 jpg

Text Sign Showing Risk Ahead. Conceptual Photo A Probability Or Threat Of Damage, Injury, Liability, Loss.
Image, 2.68MB, 6000 × 4005 jpg

Woman Making Word Risk With Wooden Cubes On Turquoise Background, Closeup
Image, 9.45MB, 6720 × 4480 jpg

Writing Note Showing Vulnerability Assessment. Business Photo Showcasing Defining Identifying Prioritizing Vulnerabilities Volume Control Knob With Marker Line And Loudness Indicator.
Image, 2.55MB, 7000 × 7000 jpg

Business Continuity Crisis Response Plan Recovery Toolbox Resources 3d Illustration
Image, 14.61MB, 5000 × 4444 jpg

Weak Password Warning Shows Online Vulnerability And Internet Threat. Risk Of Cybersecurity Breach - 3d Illustration
Image, 3.86MB, 4000 × 3000 jpg
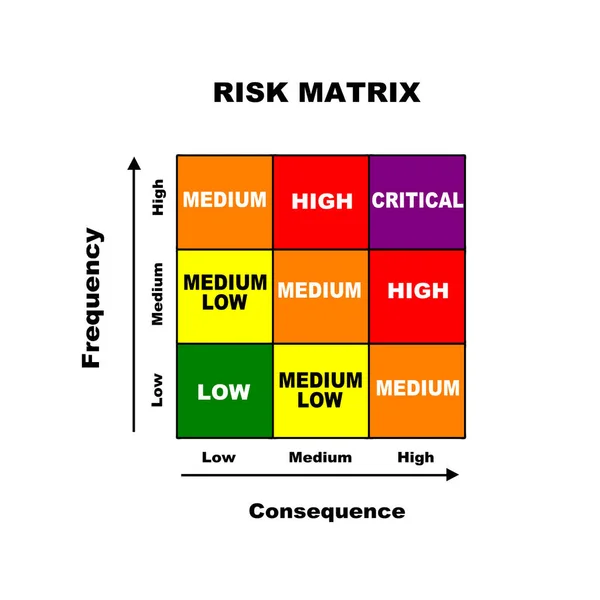
A Full-colour Risk Matrix Consisting Of Nine Possible Outcomes (3X3) With Consequences On The Horizontal And Frequency On The Vertical Axes, Isolated On A White Background.
Image, 0.48MB, 2000 × 2000 jpg

Text Sign Showing Vulnerability. Conceptual Photo State Of Being Exposed To The Possibility Of Being Attacked Elements Of This Image Furnished By NASA.
Image, 3.84MB, 6000 × 4005 jpg
Page 1 >> Next