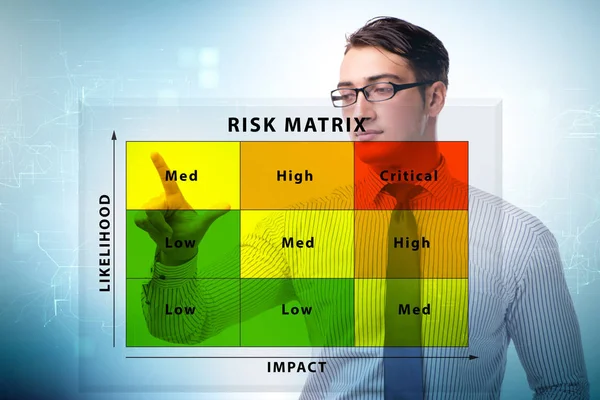
Stock image Critical Data

Critical Data - Data That Organizations Deem Essential For Success, Text Concept Button On Keyboard
Image, 8.6MB, 5760 × 3840 jpg

Torso Of A Manager Is Locking One Virtual Lock In A Lineup Of Open Padlocks. Business Metaphor And Technology Concept For Cyber Security, Critical Data Streaming, Encryption And Personal Information.
Image, 0MB, 7680 × 3840 jpg

Word Writing Text Secure Messaging. Business Photo Showcasing Protect Critical Data When Sent Beyond The Corporate Border
Image, 3.28MB, 5500 × 3669 jpg

The Word Mistake Word Written On Notepad, Eye Glasses And Pen On Crochet Carpet. Education And Business Concept
Image, 7.92MB, 4878 × 2640 jpg

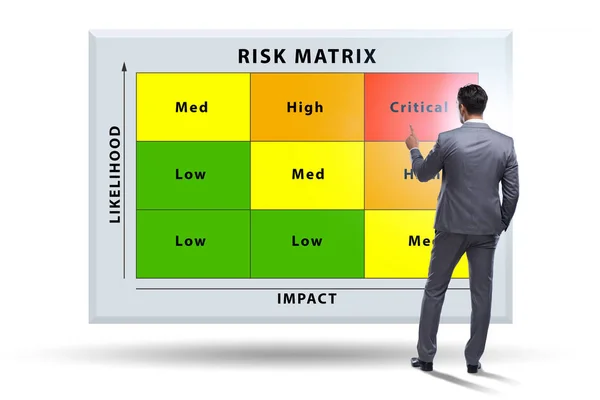
Risk Assessment And Safety Checklist Business Evaluation Tiny Person Concept. Company Document Inspection For Possible Threats And Problem Points For Investment And Finances Vector Illustration.
Vector, 0.46MB, 6000 × 3140 eps

The Hard Drive In The Computer Server Is Close-up. Data Storage Is Performed On Media. Selective Focus
Image, 5.18MB, 4649 × 3000 jpg

Open Hard Drive Secured With An Iron Chain And Padlock. Cyber Security Concept. Data Of Hard Drive Secured By Padlock
Image, 7.67MB, 5568 × 3712 jpg
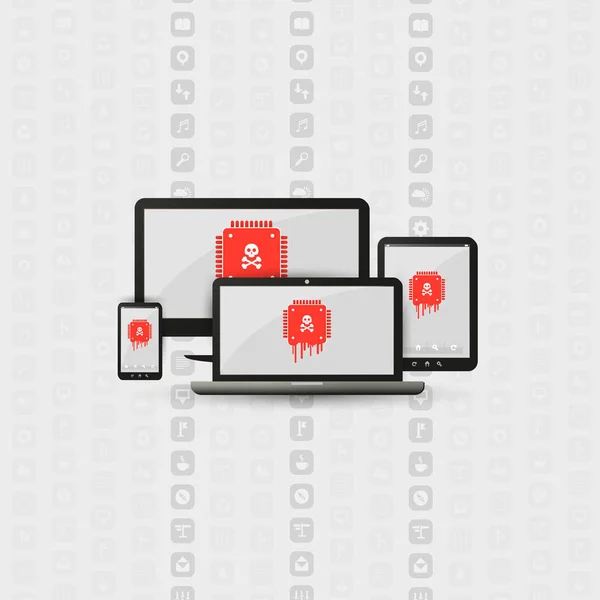
Processor Affected By Meltdown & Spectre Critical Security Vulnerabilities, Which Enable Cyber Attacks, Password Or Personal Data Leak On Computers, Servers, Mobile Devices And Cloud Services
Vector, 1.98MB, 5000 × 5000 eps

Big Data Disaster Recovery Concept. Backup Plan. Data Loss Prevention On A Virtual Screen
Image, 2.51MB, 3988 × 2657 jpg

Password Or Data Leak In Computers And Devices Due To CPU Bugs And Vulnerabilities - IT Security Concept Design
Vector, 3.42MB, 5000 × 5000 eps

Laptop Equipped With A Processor Affected By Meltdown & Spectre Critical Security Vulnerabilities, Which Enable Cyber Attacks, Password Or Personal Data Leak On Computers And Mobile Devices
Vector, 1.28MB, 5000 × 5000 eps

Cloud Computing Security Business Metaphor In Blue Colors. Corporate Arm Reaching Out To A Lock Symbol Inside A Cloud Icon. The Padlock Repeats On Cellphone, Tablet PC And Laptop Within The Network.
Image, 0MB, 6048 × 4616 jpg
Glitching Computer Screen, Glitch Programming Code. Virtual Environment, Programm Function Failure And Data Loss, Critical Code Mistake, Hacker Attack Or Hardware Malfunction Concept Vector Background
Vector, 13.49MB, 6360 × 4403 eps

Processor Affected By Meltdown & Spectre Critical Security Vulnerabilities, Which Enable Cyber Attacks, Password Or Personal Data Leak On Computers, Servers, Mobile Devices And Cloud Services
Vector, 1.25MB, 5000 × 5000 eps

Business Data Protection Analysis. Hand Holding Magnifying Glass For Seeing Document Folder Encrypted Protected Critical Important Document Data. Vector Illustration Business Data Privacy Concept.
Vector, 4.26MB, 4000 × 4000 eps

Laptop Equipped With A Processor Affected By Meltdown & Spectre Critical Security Vulnerabilities, Which Enable Cyber Attacks, Password Or Personal Data Leak On Computers And Mobile Devices
Vector, 1.42MB, 5000 × 5000 eps

Big Data Disaster Recovery Concept. Backup Plan. Data Loss Prevention On A Virtual Screen.
Image, 2.16MB, 3988 × 2657 jpg
Analysis Concept Icon. Creative Thinking Types. Checking Incoming Datum. Filtering All Information Idea Thin Line Illustration. Vector Isolated Outline RGB Color Drawing. Editable Stroke
Vector, 0.34MB, 5000 × 5000 eps

Conceptual Hand Writing Showing Cyber Incident. Business Photo Text Warning That There May Be A Threat To Information Security Elements Of This Image Furnished By NASA.
Image, 3.26MB, 6000 × 4005 jpg
Page 1 >> Next