Stock image Cyber Spies

Conceptual Hand Writing Showing Cyber Warfare. Business Photo Text Virtual War Hackers System Attacks Digital Thief Stalker.
Image, 4.1MB, 6000 × 4005 jpg

Text Sign Showing Cyber Warfare. Conceptual Photo Virtual War Hackers System Attacks Digital Thief Stalker.
Image, 3.91MB, 6000 × 4005 jpg

Conceptual Hand Writing Showing Cyber Warfare. Business Photo Text Virtual War Hackers System Attacks Digital Thief Stalker.
Image, 5.51MB, 6000 × 4005 jpg

Text Sign Showing Cyber Warfare. Conceptual Photo Virtual War Hackers System Attacks Digital Thief Stalker.
Image, 3.6MB, 6000 × 4005 jpg

Writing Displaying Text Cyber Warfare. Business Overview Virtual War Hackers System Attacks Digital Thief Stalker Writing Online Research Text Analysis, Transcribing Recorded Voice Email
Image, 3.49MB, 6000 × 4005 jpg

Word Writing Text Cyber Warfare. Business Concept For Virtual War Hackers System Attacks Digital Thief Stalker.
Image, 1.43MB, 3988 × 2662 jpg

Sign Displaying Cyber Warfare. Business Overview Virtual War Hackers System Attacks Digital Thief Stalker Typing Online Tourist Guidebook, Searching Internet Ideas And Designs
Image, 2.44MB, 6000 × 4005 jpg
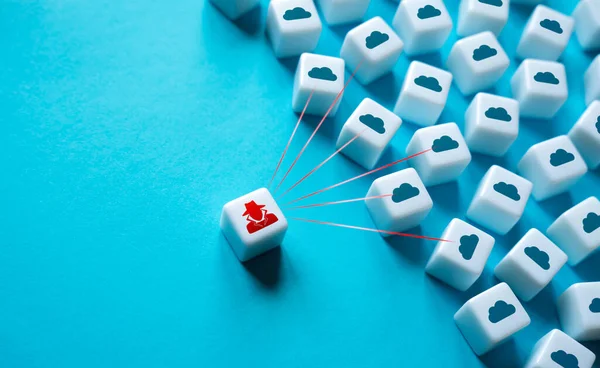
Hacker Infiltrates Cloud Network Infrastructure. Break Through Defense System. Industrial Espionage. Threat Of Leakage Of Personal Data And Corporate Information. Intrusion, Unauthorized Connection.
Image, 9.57MB, 5580 × 3426 jpg

Cyber Intelligence Team Defending Against Cyber Threats And Espionage. Governmental Hacker Using Advanced Technology To Access Information And Secure Networks, Monitors High Tech Facility. Camera A.
Image, 18.87MB, 7373 × 4147 jpg

Dangerous Spies Brainstorming Ways To Do International Espionage Warfare On Other Countries After Being Contracted By Government, Using Their Programming Skills To Infiltrate Past Firewalls
Image, 16.95MB, 7373 × 4147 jpg

Purging Industrial Spies And Malicious Hackers From A Group Of Employees. Industrial And Financial Espionage. Protect Business From Sabotage And Data Leaks. Screening Of Staff For Hostile Elements.
Image, 8.09MB, 3808 × 5606 jpg

Spies In Secret Hideout Trying To Steal Valuable Data By Hacking Governmental Websites But Getting Their Attacks Rejected By Strong Security, Seeing Access Denied Error Message On Screen
Image, 16MB, 7373 × 4147 jpg

Group Of Professional Spies Doing International Espionage Warfare On Other Countries, Hired By Their Government, Using High Tech Computer Systems To Infiltrate Past Protection Firewalls
Image, 17.3MB, 7373 × 4147 jpg

Corporate Network Is Under Surveillance By Spies. Protect Sensitive Business Information With Powerful Protection. Figureheads, Double Agents. Checking Employees For Data Leaks, Suspicious Activity
Image, 4.85MB, 5056 × 3462 jpg

Teamworking Spies Contracted By Government To Do International Espionage Warfare On Other Countries, Using Advanced Technology Computer Equipment To Infiltrate Past Protection Firewalls
Image, 15.44MB, 7373 × 4147 jpg

A Hacker Infiltrates The Team. Industrial And Financial Espionage. Protect Business From Sabotage And Data Leaks. Screening Of Staff For Hostile Elements.
Image, 6.1MB, 4793 × 3295 jpg
Page 1 >> Next



