Stock image Cyber Threat

Cyber Threat Intelligence Online Protection 3d Rendering Shows Online Malware Protection Against Ransomware Scams And Risks
Image, 2.93MB, 3740 × 3000 jpg

A Silhouette Of A Hacker With A Black Hat In A Suit Enters A Hallway
Image, 12.66MB, 6000 × 3375 jpg

Isometric Vector Internet Hacker Attack And Personal Data Security Concept. Computer Security Technology. E-mail Spam Viruses Bank Account Hacking. Hacker Working On A Code. Internet Crime Concept.
Vector, 5.55MB, 5000 × 3750 eps

Digital Skull And Crossbones On Binary Code. Eps8. RGB. Global Colors
Vector, 6.75MB, 5984 × 4189 eps

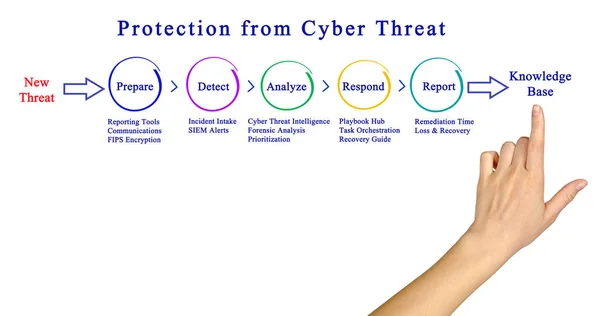
IT Manager Pressing IT RISK On A Touch Screen. Three Unlocked Lock Icons Embedded In A Hexagonal Virtual Security Structure Do Light Up To Represent A Possible Threat Or Exploit Of Vulnerabilities.
Image, 0MB, 7680 × 3840 jpg

Creative Glowing Circuit Antivirus Background. Cyberspace And Encryption Concept. 3D Rendering
Image, 4.96MB, 4500 × 3000 jpg
Cyber Security Icon Vector. Security Logo Artificial Intelligence Keyhole Symbol Speed Internet Technology Sign For Graphic Design, Logo, Web Site, Social Media, Mobile App, Ui Illustration
Vector, 5.73MB, 4167 × 4167 eps

Computer Crime Concept. Internet Phishing A Login And Password Concept
Vector, 1.36MB, 2700 × 2100 eps

Rear View Of Businessman Using Immersive Digital Security Interface Over Night City Background. Toned Image Double Exposure
Image, 7.86MB, 6148 × 4000 jpg

Coputer Internet Cyber Security Background. Cyber Crime Vector Illustration. Digital Lock
Vector, 31.88MB, 5000 × 2785 eps
Page 1 >> Next