Stock image Cybersecurity Risks

Identity Threat Detection And Response And Cloud Infrastructure Entitlement Management Concept - ITDR And CIEM - New Cloud-based Cybersecurity Solutions - 3D Illustration
Image, 16.32MB, 8845 × 5200 jpg

Threat Detection And Response - TDR - Advanced Digital Threat Detection And Response Concept With Digital Black Widow Spider On The Crosshairs - Cybersecurity Risks In Organizations
Image, 11.86MB, 6500 × 3656 jpg

Cloud Workload Security And Cloud Workload Protection Concept - CWS And CWP - The Practice Of Protecting Workloads Run On Cloud Resources - 3D Illustration
Image, 9.87MB, 7872 × 4642 jpg

Digital Threat Detection And Response Concept - TDR - Cybersecurity Risks - Digital Black Widow Spider On Virtual Crosshairs
Image, 11.55MB, 6500 × 3656 jpg

Cyber Threat Intelligence Online Protection 3d Rendering Shows Online Malware Protection Against Ransomware Scams And Risks
Image, 1.69MB, 3000 × 3300 jpg
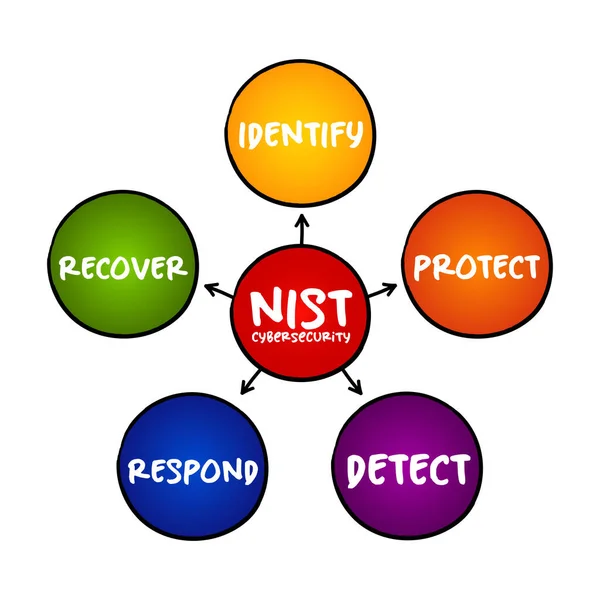
NIST Cybersecurity Framework - Set Of Standards, Guidelines, And Practices Designed To Help Organizations Manage IT Security Risks, Mind Map Concept For Presentations And Reports
Vector, 0.95MB, 8376 × 8376 eps

NIST Cybersecurity Framework - Set Of Standards, Guidelines, And Practices Designed To Help Organizations Manage IT Security Risks, Mind Map Concept For Presentations And Reports
Vector, 1.2MB, 9657 × 7297 eps
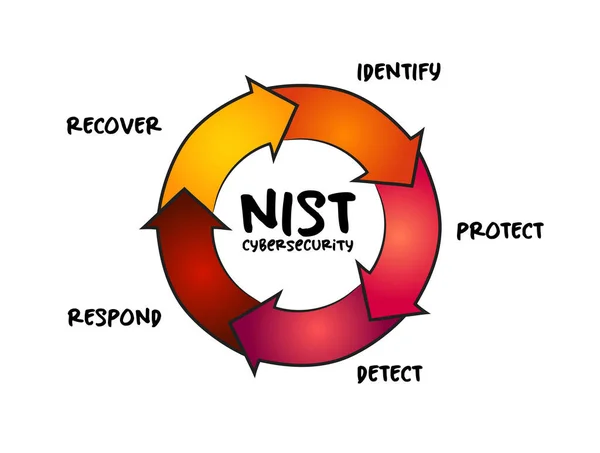
NIST Cybersecurity Framework - Set Of Standards, Guidelines, And Practices Designed To Help Organizations Manage IT Security Risks, Process Concept For Presentations And Reports
Vector, 1.26MB, 9657 × 7297 eps

NIST Cybersecurity Framework - Set Of Standards, Guidelines, And Practices Designed To Help Organizations Manage IT Security Risks, Process Concept For Presentations And Reports
Vector, 1.25MB, 9657 × 7297 eps

NIST Cybersecurity Framework - Set Of Standards, Guidelines, And Practices Designed To Help Organizations Manage IT Security Risks, Text Concept On Notepad
Image, 6.37MB, 5760 × 3840 jpg

NIST Cybersecurity Framework - Set Of Standards, Guidelines, And Practices Designed To Help Organizations Manage IT Security Risks, Text On Card Concept
Image, 2.49MB, 5622 × 3834 jpg

NIST Cybersecurity Framework - Set Of Standards, Guidelines, And Practices Designed To Help Organizations Manage IT Security Risks, Text Concept On Notepad
Image, 6.5MB, 5760 × 3840 jpg

Website Hacked Cyber Security Alert 3d Illustration Shows Online Site Data Risks. Election Hacking Attacks On The Usa In 2018 And 2020 From Russia
Image, 6.2MB, 3300 × 3000 jpg

Vector Cyber Care Concept - Data Protection From Espionage, Hacking, Viruses, Attacks, Cybercrime, Bullying, Breach And Another Dangers
Vector, 9.15MB, 5905 × 3720 eps

NIST Cybersecurity Framework - Set Of Standards, Guidelines, And Practices Designed To Help Organizations Manage IT Security Risks, Text Concept For Presentations And Reports
Vector, 2.9MB, 9657 × 7297 eps

Digital Text With Phrases Like CYB3R A7TACK And SECURITY Displayed On Screen. Dark Background With Various Letters And Numbers, Suggesting A Cybersecurity Theme
Image, 0.24MB, 4096 × 2160 jpg

Businessman With A Concerned Expression Is Reflecting On The Potential Benefits And Risks Of Technological Advancements
Image, 8.75MB, 6720 × 4480 jpg

Businessman Using AI Technology For Cybersecurity Enhances Threat Detection And Response Capabilities, Safeguarding Digital Environments From Evolving Risks.
Image, 8.6MB, 6924 × 4024 jpg

Data Center Software Developer Ensuring Safety And Security Of Database Using Tablet. Cybersecurity Professional In Server Farm Preventing Unauthorized Access Posing Risks For Company
Image, 5.75MB, 5275 × 3517 jpg

Data Center Manager Ensuring Safety And Security Of Database Using Notebook. African American Man In Server Farm Preventing Unauthorized Access And Suspicious Activities Posing Risks For Business
Image, 5.35MB, 3505 × 5258 jpg

Threats And Dangers. Warnings And Red Flags Concept. Cybersecurity. Safety At Work In Production. Safety Regulations. Cautions
Image, 8.98MB, 3912 × 5692 jpg

A Person Wearing A Pirate Hat Sits At A Sleek Desk With A Laptop, Focused On Engaging In Illicit Online Activities. Surrounding The Workspace Are Notebooks And A Smartphone, Reflecting A Casual Yet Deceptive Atmosphere Of Modern Cybercrime.
Image, 7.31MB, 5760 × 3840 jpg

Prevent Industrial And Financial Espionage, Virus Threats, Network Surveillance. Eliminate The Risks Of Sabotage And Data Theft. Firewalls And Antivirus Software. Intrusion Detection Systems IDS
Image, 7.79MB, 4898 × 3497 jpg

An Illustration Of A Ban On Artificial Intelligence, Featuring A Blue Chip With The AI Label Crossed Out By A Red Prohibition Sign. Restricting AI In Various Fields
Vector, 0.25MB, 4000 × 4000 eps

Data Center System Administrator Ensuring Safety And Security Of Database Using Laptop. IT Staff Member In Server Farm Preventing Unauthorized Access Posing Risks For Company
Image, 5.3MB, 3517 × 5275 jpg

Container Security Concept - Practice Of Protecting Containerized Applications From Potential Risks - 3D Illustration
Image, 23.11MB, 9584 × 5298 jpg

A Large Padlock Is Prominently Displayed Against Dark Background With Scattered Text. The Text Includes Words Like MALWARE And CYBERCRIME, Suggesting A Theme Of Cybersecurity
Image, 0.23MB, 4096 × 2160 jpg
Digital Lock Icon Surrounded By Code And Warning Messages. Complex Network Of Data And Cybersecurity Threats Showing In Background
Image, 0.46MB, 4096 × 2160 jpg

The Interconnected Warning Signs Highlight The Potential Threats And Vulnerabilities Lurking Online, Emphasizing The Importance Of Cybersecurity Measures.
Image, 5.17MB, 4928 × 3264 jpg

Businesswoman In Formal Wear Signing The Contract To Prevent Probability Of Risks In Cyber Security. Checking The Phone. Padlock Hologram Icons Over The Working Desk.
Image, 12.4MB, 6000 × 4000 jpg

Businessman Using AI Technology For Cybersecurity Enhances Threat Detection And Response Capabilities, Safeguarding Digital Environments From Evolving Risks.
Image, 11.07MB, 6048 × 4024 jpg

Levels Of Protection. Cyber Security. Protection Upgrade. Increasing Defense. Security Levels And Safety Margin.
Image, 8.57MB, 5125 × 3546 jpg

IT Technician Speaking At Tech Event, Explaining Impact Of AI Technology On World. Woman Presenting Risks And Threats Associated With AI During Conference, Pointing To Screen
Image, 6.09MB, 5446 × 3631 jpg
Page 1 >> Next
