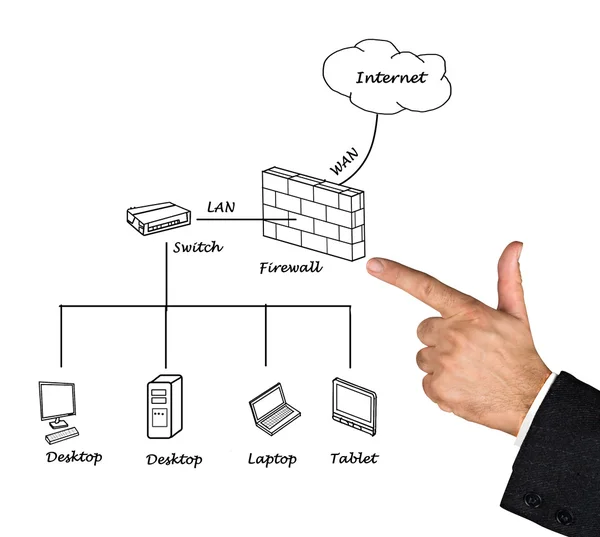
Stock image Diagram Of It Security

Image, 5.8MB, 8000 × 4000 jpg

Image, 1.08MB, 2712 × 2340 jpg
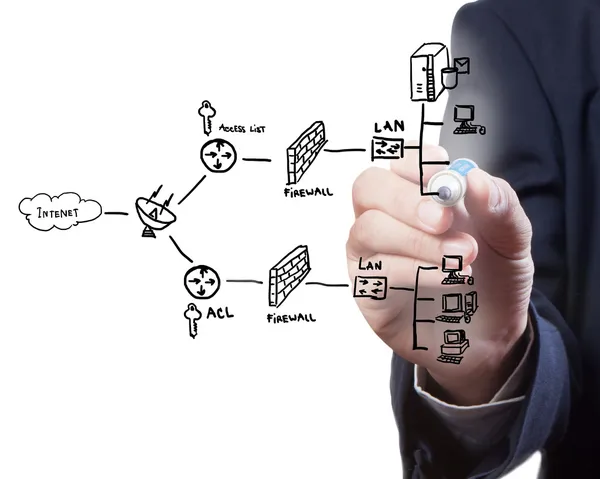
Image, 2.99MB, 4680 × 3744 jpg
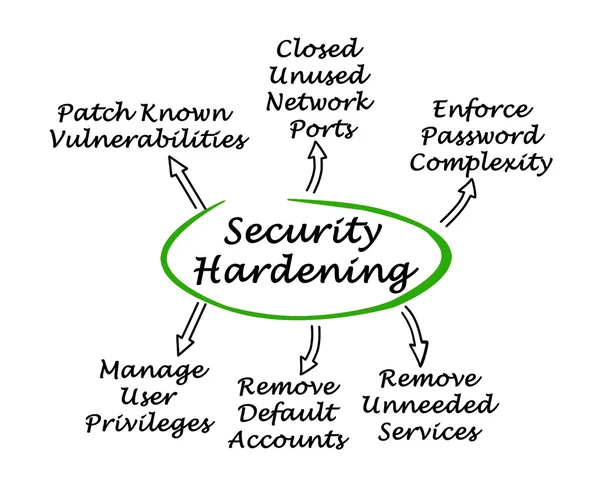
Image, 0.79MB, 2240 × 1830 jpg

Image, 2.54MB, 4143 × 3496 jpg
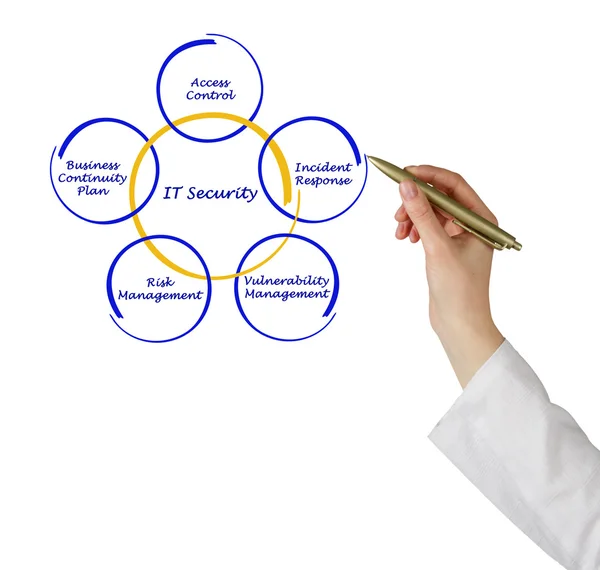
Image, 1.64MB, 3030 × 2878 jpg
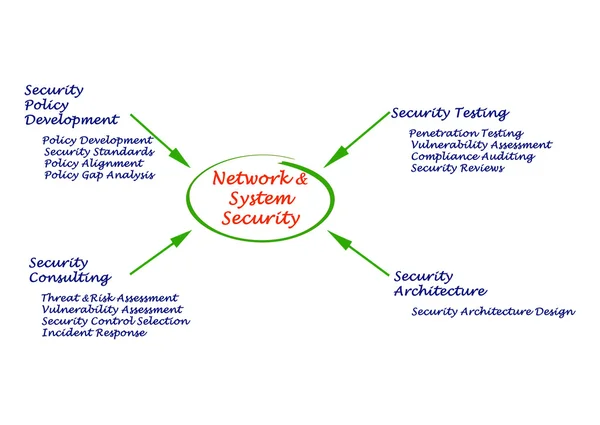
Image, 0.96MB, 2399 × 1702 jpg

Vector, 4.86MB, 6189 × 4532 eps

Image, 1.36MB, 2735 × 2381 jpg
Image, 1.77MB, 2912 × 2557 jpg
Image, 0.85MB, 2000 × 2000 jpg
Image, 3.72MB, 5225 × 4528 jpg

Image, 4.26MB, 3711 × 3673 jpg

Image, 1.94MB, 3600 × 2400 jpg
Image, 3.46MB, 4756 × 4173 jpg
Image, 1.61MB, 3600 × 2400 jpg
Image, 2.98MB, 4933 × 4024 jpg
Image, 6.16MB, 4200 × 3600 jpg

Image, 2.1MB, 3696 × 3058 jpg

Image, 4.8MB, 4679 × 4193 jpg
Image, 1.64MB, 3600 × 2400 jpg

Image, 1.67MB, 2370 × 2663 jpg
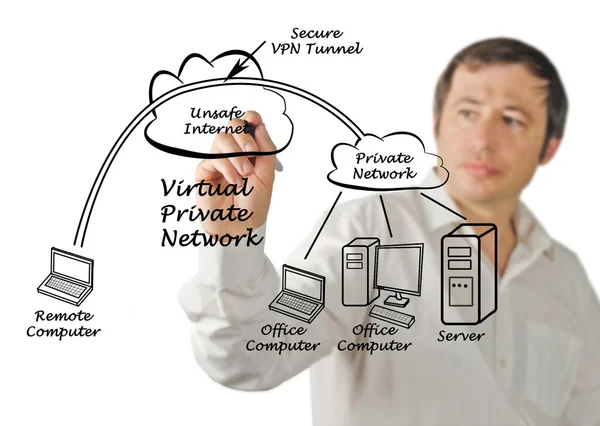
Image, 3.47MB, 4844 × 3446 jpg

Image, 1.56MB, 2416 × 2268 jpg

Image, 2.58MB, 3486 × 2664 jpg
Image, 5.62MB, 4200 × 3600 jpg
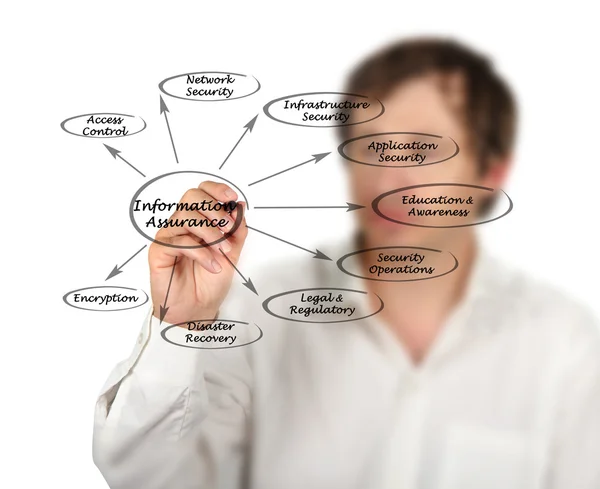
Image, 2.41MB, 3756 × 3063 jpg

Image, 2.25MB, 3035 × 2878 jpg

Image, 1.74MB, 3396 × 3186 jpg

Image, 2.38MB, 4916 × 3182 jpg

Image, 3.6MB, 5257 × 3916 jpg
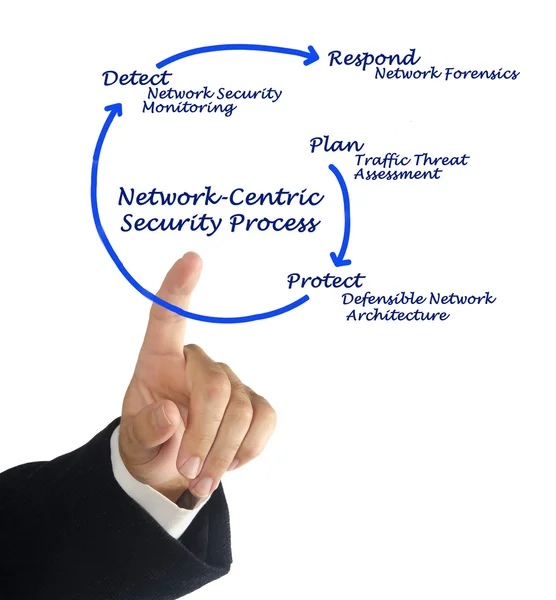
Image, 3.46MB, 3859 × 4164 jpg

Image, 3.14MB, 4014 × 3633 jpg

Image, 3.01MB, 4580 × 4037 jpg
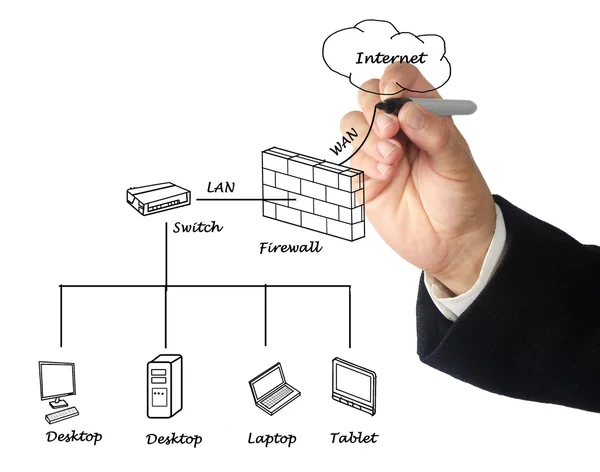
Image, 2.16MB, 3563 × 2808 jpg

Image, 1.38MB, 2735 × 2088 jpg

Image, 2.52MB, 4778 × 3520 jpg

Image, 2.19MB, 2432 × 3436 jpg

Image, 4.54MB, 4862 × 4475 jpg

Vector, 16.48MB, 6809 × 3000 eps

Image, 3.96MB, 4162 × 2858 jpg

Image, 1.79MB, 2774 × 2807 jpg

Image, 2.89MB, 4613 × 3108 jpg
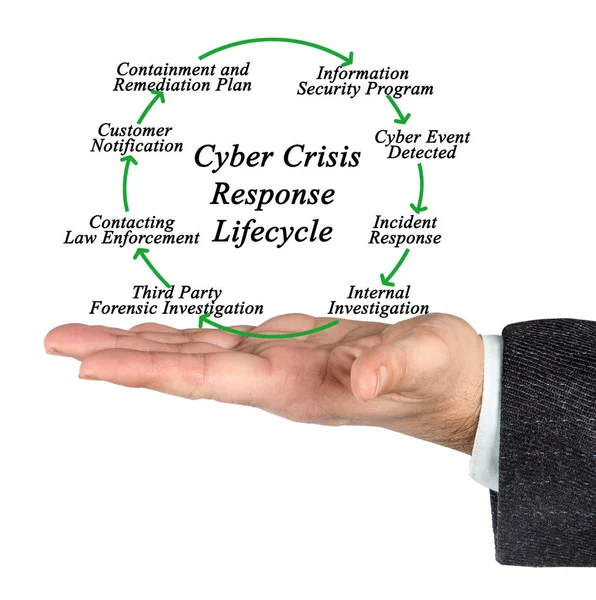
Image, 1.55MB, 2865 × 2883 jpg
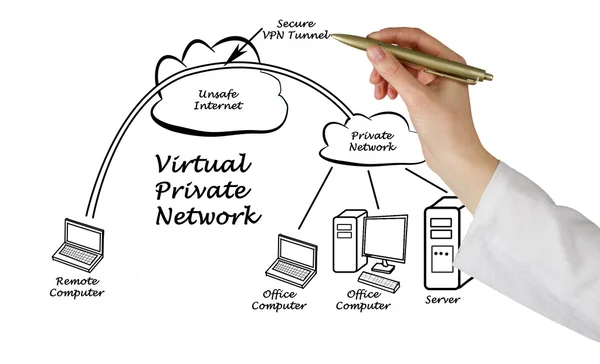
Image, 2.78MB, 5259 × 3192 jpg
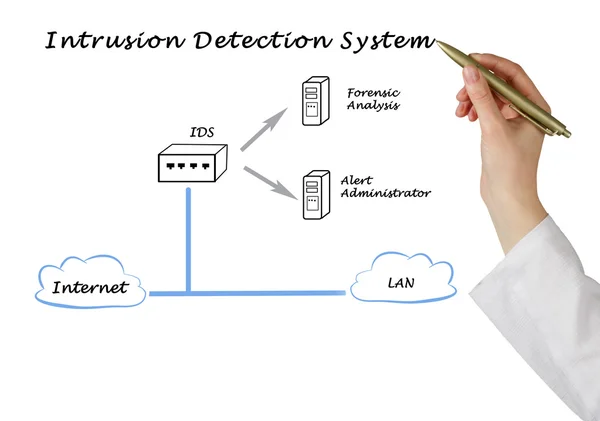
Image, 1.83MB, 4235 × 2973 jpg
Image, 1.74MB, 3560 × 3187 jpg

Image, 4.05MB, 4112 × 2861 jpg

Vector, 0.43MB, 5000 × 3750 eps

Image, 5.26MB, 3600 × 3600 jpg

















































