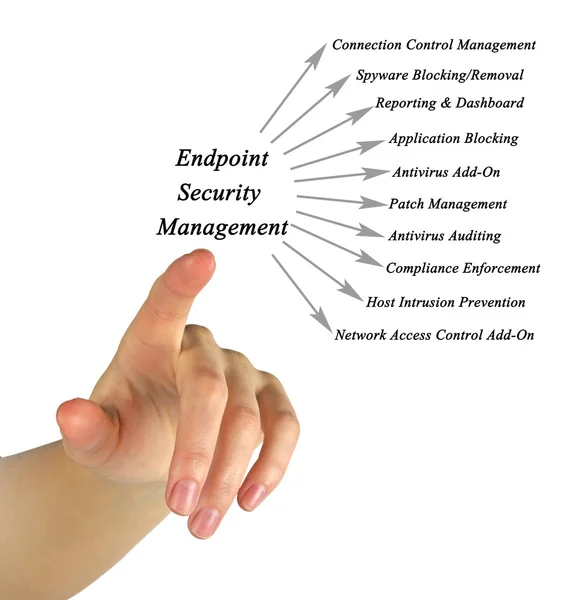
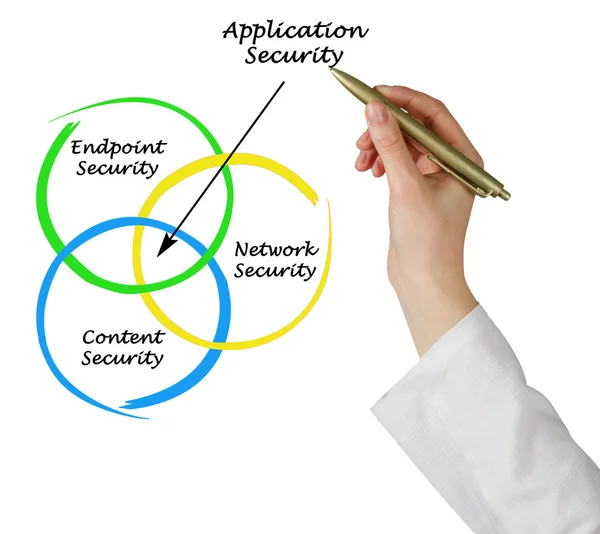
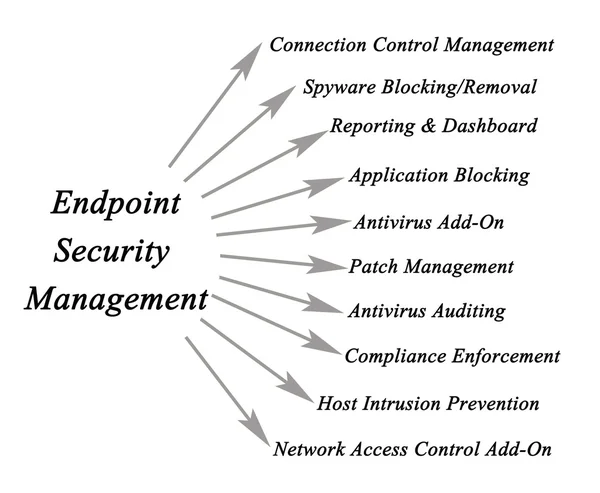
Stock image Endpoint Security

Manager Is Pushing ENDPOINT SECURITY On A Virtual Touch Screen Interface. Information Technology And Security Concept For Software And Technology Protecting Corporate Computing Networks.
Image, 0MB, 7680 × 3840 jpg

Cloud-based Cybersecurity Software - Endpoint Security Solutions Concept With Virtual Shield And Laptop Connected To The Digital Cloud - 3D Illustration
Image, 13.14MB, 8775 × 6045 jpg

Endpoint Security Written On Blue Key Of Metallic Keyboard. Finger Pressing Key
Image, 7.29MB, 5242 × 3744 jpg
Endpoint Security Linear Desktop Icon. Device Management. Antivirus Protection. Pixel Perfect 128x128, Outline 4px. GUI, UX Design. Isolated User Interface Element For Website. Editable Stroke
Vector, 0.47MB, 5000 × 5000 eps

Identity Threat Detection And Response And Cloud Infrastructure Entitlement Management Concept - ITDR And CIEM - New Cloud-based Cybersecurity Solutions - 3D Illustration
Image, 16.32MB, 8845 × 5200 jpg

Endpoint Security - Endpoint Protection Concept - Multiple Devices Secured Within A Network - Security Cloud - Cloud-based Cybersecurity Software Solutions - 3D Illustration
Image, 9.84MB, 8535 × 5261 jpg

Cloud-based Cybersecurity Solutions Concept - Endpoint Protection - Devices Protected Within A Digital Network - 3D Illustration
Image, 7.41MB, 6978 × 4650 jpg

Business And Finance. On A White Background, There Is A Calculator, A Pen And A Black Notebook With The Inscription - ENDPOINT SECURITY
Image, 5.22MB, 5906 × 3898 jpg

Endpoint Security Safe System Shows Safeguard Against Virtual Internet Threat - 3d Illustration
Image, 6.6MB, 3960 × 3000 jpg

Endpoint Security Safe System Shows Safeguard Against Virtual Internet Threat - 2d Illustration
Image, 6.45MB, 3600 × 3000 jpg

Endpoint Security Safe System Shows Safeguard Against Virtual Internet Threat - 2d Illustration
Image, 4.46MB, 3486 × 3000 jpg

Cloud-based Cybersecurity Solutions - Secure Corporate And Institutional Networks - Endpoint Protection - Security Service Edge And Secure Access Service Edge - 3D Illustration
Image, 13.96MB, 9584 × 5298 jpg

Endpoint Security Platform - Cloud-based Endpoint Protection Concept - Innovative Cybersecurity Solutions - 3D Illustration
Image, 9.2MB, 6700 × 4375 jpg

Internet And Security Concept. There Is A Router Connected To The Network On The Table, Next To A Plaque With The Inscription - Endpoint Security
Image, 7.09MB, 5906 × 3898 jpg

Endpoint Security Safe System Shows Safeguard Against Virtual Internet Threat - 3d Illustration
Image, 7.93MB, 3600 × 3000 jpg

Endpoint Security Safe System Shows Safeguard Against Virtual Internet Threat - 3d Illustration
Image, 7.77MB, 4000 × 3000 jpg

Conceptual Hand Writing Showing Endpoint Security. Concept Meaning The Methodology Of Protecting The Corporate Network
Image, 3.86MB, 6000 × 4005 jpg

Inspiration Showing Sign Endpoint Security. Word For The Methodology Of Protecting The Corporate Network Architect Interviewing Client, Reporther Gathering Important Informations
Image, 3.03MB, 6000 × 4005 jpg

Phishing Email, Cyber Criminals, Hackers, Phishing Email To Steal Personal Data, Hacked Laptop, Malware, Infected Email, Scene Of A Person Working On A Laptop With An Infected Email On The Screen
Vector, 0.4MB, 10942 × 6022 ai

Cybersecurity System, Hosting On Server, Accepted Secure Wireless Connection Global GPS, Data Update Protection With Shield. Online Security Trendy Red Black Thin Line Icons Set Vector Illustration.
Vector, 1.36MB, 9888 × 4409 eps

Rows Of Locks With A Digital Background, Representing Cybersecurity And The Defense Of Sensitive Information.
Image, 6.12MB, 5824 × 3264 jpg

3D Phishing Email, Cyber Criminals, Hackers, Phishing Email To Steal Personal Data, Hacked Laptop, Malware, Infected Email
Vector, 3.72MB, 5235 × 4708 ai
Bright Orange Digital Lock Icon With Radiating Lines Amidst A Futuristic Blue And Red Grid, Symbolizing Cutting-edge Cybersecurity Measures.
Image, 9.38MB, 5824 × 3264 jpg

Cyber Threat Intelligence Concept - Collection And Analysis Of Information About Ongoing And Potential Cyber Attacks - 3D Illustration
Image, 11.85MB, 8320 × 5010 jpg

Endpoint Security Safe System Shows Safeguard Against Virtual Internet Threat - 2d Illustration
Image, 4.49MB, 3300 × 3000 jpg

Zero Trust Architecture And Zero Trust Network Architecture - ZTA And ZTNA - IT Security Model Based On Maintaining Strict Access Controls And Not Trusting Anyone By Default - Conceptual Illustration
Image, 10.45MB, 6324 × 3437 jpg

Zero Trust Network Architecture And Zero Trust Architecture - ZTA And ZTNA - Data-centric Cybersecurity Solutions That Protect Resources Over A Network Perimeter - Conceptual Illustration
Image, 9.54MB, 7824 × 4610 jpg

Endpoint Security Safe System Shows Safeguard Against Virtual Internet Threat - 2d Illustration
Image, 7.16MB, 3787 × 3000 jpg

STUTTGART, GERMANY - Mar 09, 2021: Mobile Phone With Logo Of Cyber Security Company CrowdStrike Holdings Inc. On Screen In Front Of Web Page. Focus On Center-left Of Phone Display.
Image, 6.14MB, 4500 × 3376 jpg

STUTTGART, GERMANY - Mar 09, 2021: Person Holding Smartphone With Logo Of US Software Company CrowdStrike Holdings Inc. On Screen In Front Of Website. Focus On Phone Display.
Image, 7.25MB, 4500 × 3375 jpg

Zero Trust - Zero Trust Network - Zero Trust Architecture - ZTA - Innovative Forms Of Cyber Security - Conceptual Illustration
Image, 11.8MB, 6500 × 3656 jpg

Application Security Monitoring Concept - Cloud-based Solutions Which Protect Against Application-level Threats By Identifying Attacks That Target Code-level Vulnerabilities - 3D Illustration
Image, 23.61MB, 9584 × 5298 jpg

STUTTGART, GERMANY - Mar 09, 2021: Person Holding Cellphone With Business Logo Of US Software Company CrowdStrike Holdings Inc. On Screen In Front Of Webpage. Focus On Phone Display.
Image, 7.84MB, 4500 × 3376 jpg

Zero Trust Technologies - Strategic Application Of Cyber Security That Secures An Enterprise By Eliminating Implicit Trust And Continuously Validating Every Digital Interaction - Conceptual Illustration
Image, 15.91MB, 8000 × 4500 jpg

STUTTGART, GERMANY - Mar 09, 2021: Person Holding Cellphone With Logo Of US Cybersecurity Company CrowdStrike Holdings Inc. On Screen In Front Of Web Page. Focus On Phone Display.
Image, 5.65MB, 4500 × 3375 jpg
Page 1 >> Next