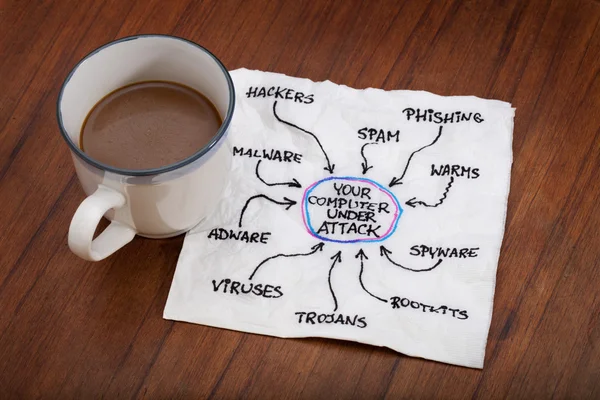
Stock image Internet Risks

Senior Villager In Plaid Shirt And Cowboy Hat Holding Smartphone With Chroma Key Screen, Offering Serious Advice On Internet Safety, Captured Against Green Background.
Image, 5.29MB, 4928 × 3264 jpg

Handwriting Text Fraud Detection. Concept Meaning Identification Of Actual Or Expected Fraud To Take Place.
Image, 3.04MB, 6000 × 4005 jpg

Businessman In Office Working With Laptop, Develop Data Protection System To Diminish Business Risks, Typing Computer. Double Exposure.
Image, 10.25MB, 6000 × 4000 jpg

A Businessman In Casual Wear Signing The Contract To Prevent Probability Of Risks In Cyber Security. Checking The Phone. Padlock Hologram Icons Over The Working Desk.
Image, 11.89MB, 6000 × 4000 jpg

Male Corporate Manager Is Touching DO ADDRESS BEHAVIORAL RISKS! On An Interactive Visual Screen. Business Challenge Metaphor And Information Technology Concept For Risks In Computer Usage Patterns.
Image, 0MB, 7680 × 3840 jpg

A Businessman In Formal Wear Signing The Contract To Prevent Probability Of Risks In Cyber Security. Padlock Hologram Icons Over The Working Desk.
Image, 10.92MB, 6000 × 4000 jpg

A Businesswoman In Casual Wear Signing The Contract To Prevent Probability Of Risks In Cyber Security. Padlock Hologram Icons Over The Working Desk.
Image, 13.12MB, 6000 × 4000 jpg

Locked Computer Safe From Virus Or Malware Attack. Laptop Computer Being Protected From Online Cyber Crime And Hacking. Computer Security Concept With A Padlock On A Keyboard. Protection Various Risks
Image, 8MB, 6000 × 4000 jpg

Website Hacked Cyber Security Alert 3d Illustration Shows Online Site Data Risks. Election Hacking Attacks On The Usa In 2018 And 2020 From Russia
Image, 6.2MB, 3300 × 3000 jpg

Smartphone With Chain Locked On White Background, Security And Privacy Concept
Image, 0.94MB, 5184 × 3456 jpg
Page 1 >> Next