Stock image Log4j

Hooded Computer Hacker In Cybersecurity Vulnerability Log4J Concept With Digital Glitch Effect
Image, 8.14MB, 5176 × 3455 jpg

Security Vulnerability Log4j. Java Code Log4j With Warning Sign. Cyberspace And Vulnerability. Vector Illustration
Vector, 2.18MB, 5557 × 3125 eps
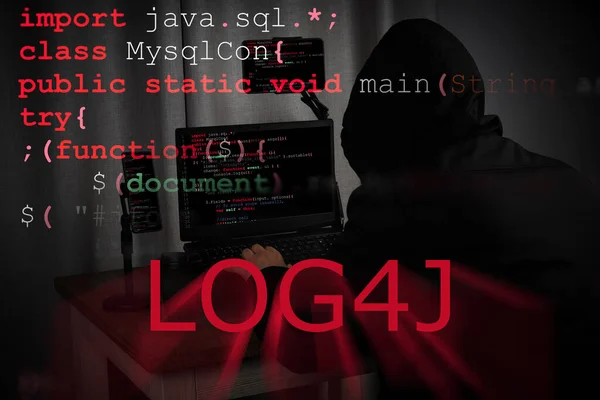
Security Breach In Log4J/Log4Shell Is One Of Biggest IT Vulnerabilities In Years. Java Source Code Of Log4j Event Recor. HACK CONCEPT
Image, 9.39MB, 5802 × 3868 jpg

Illustration Of Log4j Vulnerability. Cybersecurity And Information Security Incidence Concept. Cyber Attack And Crime
Image, 1.49MB, 6000 × 4000 jpg

Illustration Of Alert Warning Sign With Digital Binary Code In The Background. Esclamation Mark. Hacker, Ransomware, Malware, Ddos Attack, Log4j, Cyber Incident Cybersecurity Systems Vulnerability Malicious Encryption Concept
Vector, 0.6MB, 6000 × 4000 ai

Smartphone In Hand Security Vulnerability Log4J. Security Vulnerability Log4j. The Concept Of Cyber Crime, Cybersecurity And Information Security Incidence. Cyber Attack And Crime.
Image, 6.72MB, 4910 × 3527 jpg

Hooded Computer Hacker In Cybersecurity Vulnerability Log4J Concept With Digital Glitch Effect
Image, 4.37MB, 5101 × 3405 jpg

Illustration Of Log4j And Log4Shell Vulnerability. Cybersecurity And Information Security Incidence Concept. Cyber Attack And Crime
Vector, 0.21MB, 5000 × 3000 ai

Illustration Of Log4j And Log4Shell Vulnerability. Cybersecurity And Information Security Incidence Concept. System Error Cyber Attack, Alert, Warning And Crime
Vector, 0.22MB, 5000 × 3000 ai

Cybersecurity Vulnerability Log4J, Security Flaw Based On Open-source Logging Library, Conceptual 2d Illustration
Image, 3.6MB, 5000 × 3000 jpg

Illustration Of Cybersecurity, World Wide Computer Controlled By A Botnet Master. Botnet Is A Number Of Internet-connected Devices, Each Of Which Is Running One Or More Bots. Network Infected With Malware, Trojan Horse, Virus, Worm
Vector, 1.28MB, 4000 × 4000 ai
Page 1 >> Next
