Stock image Network Access Control

Businessman Fingerprint Scan And Pressing Technology Lock Security For Unlock All Information Technology Device Over Blurred Data Center Server Room Background
Image, 3.38MB, 6000 × 4000 jpg
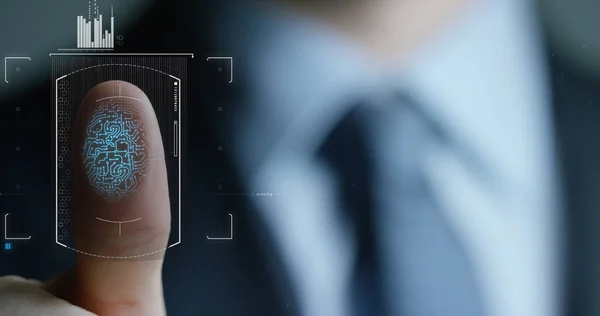
Slow Motion Of Scan Fingerprint Biometric Identity And Approval. Concept Of The Future Of Security And Password Control Through Fingerprints In An Advanced Technological Future And Cybernetic
Image, 4.45MB, 4096 × 2160 jpg

Futuristic Digital Processing Of Biometric Fingerprint Scanner. Concept Of Surveillance And Security Scanning Of Digital Programs And Fingerprint Biometrics. Cyber Futuristic Applications.
Image, 2.45MB, 4096 × 2160 jpg

Slow Motion Of Scan Fingerprint Biometric Identity And Approval. Concept Of The Future Of Security And Password Control Through Fingerprints In An Advanced Technological Future And Cybernetic
Image, 4.66MB, 4096 × 2160 jpg

Business, Technology, Internet And Network Concept. Business Man Working On The Tablet Of The Future, Select On The Virtual Display: Access Control
Image, 6.15MB, 6000 × 3000 jpg

Slow Motion Of Scan Fingerprint Biometric Identity And Approval. Concept Of The Future Of Security And Password Control Through Fingerprints In An Advanced Technological Future And Cybernetic
Image, 4.37MB, 4096 × 2160 jpg

Door Access Control. Staff Holding A Key Card To Lock And Unlock Door At Control Room Or Data Center. The Concept Of Data Security Or Data Access Control.
Image, 6.76MB, 5489 × 3659 jpg

Finger Touching Virtual Panel Scanning Fingerprint For Verification, Blue Background
Image, 5.72MB, 6413 × 3111 jpg

Door Access Control By Fingerprint Scanner, Facial Recognition And Key Card, Security Concept.
Image, 11.66MB, 5000 × 3333 jpg

Slow Motion Of Scan Fingerprint Biometric Identity And Approval. Concept Of The Future Of Security And Password Control Through Fingerprints In An Advanced Technological Future And Cybernetic
Image, 5.17MB, 4096 × 2160 jpg

Graphics Of Latest Digital Technology Protection Data Padlock Security On The Virtual Display. Businessman With Lock To Secure.
Image, 7.82MB, 6000 × 4005 jpg

Staff Push Down Electronic Control Machine With Finger Scan To Access The Door Of Control Room Or Data Center. The Concept Of Data Security Or Data Access Control.
Image, 7.55MB, 5052 × 3840 jpg

Graphics Of Latest Digital Technology Protection Data Padlock Security On The Virtual Display. Businessman With Lock To Secure.
Image, 17.01MB, 6000 × 4005 jpg

Graphics Of Latest Digital Technology Protection Data Padlock Security On The Virtual Display. Businessman With Lock To Secure.
Image, 12.48MB, 6000 × 4005 jpg

Graphics Of Latest Digital Technology Protection Data Padlock Security On The Virtual Display. Businessman With Lock To Secure.
Image, 14.63MB, 6000 × 4005 jpg

Slow Motion Of Scan Fingerprint Biometric Identity And Approval. Concept Of The Future Of Security And Password Control Through Fingerprints In An Advanced Technological Future And Cybernetic
Image, 4.57MB, 4096 × 2160 jpg

Slow Motion Of Scan Fingerprint Biometric Identity And Approval. Concept Of The Future Of Security And Password Control Through Fingerprints In An Advanced Technological Future And Cybernetic
Image, 4.36MB, 4096 × 2160 jpg

Staff Push Down Electronic Control Machine With Finger Scan To Access The Door Of Control Room Or Data Center. The Concept Of Data Security Or Data Access Control.
Image, 7.73MB, 5322 × 3749 jpg

Staff Push Down Electronic Control Machine With Finger Scan To Access The Door Of Control Room Or Data Center. The Concept Of Data Security Or Data Access Control.
Image, 7.17MB, 5423 × 3615 jpg

Staff Push Down Electronic Control Machine With Finger Scan To Access The Door Of Control Room Or Data Center. The Concept Of Data Security Or Data Access Control.
Image, 5.51MB, 4837 × 3225 jpg

Identity And Access Management Technologies Concept - IAM And IdAM Through Multi-factor Authentication As Represented By Password Field And Digital Key And Virtual Padlock - 3D Conceptual Illustration
Image, 9.98MB, 7930 × 5420 jpg

Identity And Access Management - IAM And IdAM - Processes And Technologies For Ensuring Appropriate Access To Technology Resources - Identification And Authentication To Provide Access To Applications And Systems Or Networks - 3D Illustration
Image, 9.15MB, 7000 × 4784 jpg

Cloud Computing Security - Vulnerability And Threat Management Solutions - Security Operations And Program Governance - New Threat Intelligence Applications - 3D Illustration
Image, 13.22MB, 9584 × 5298 jpg

Abstract Security, Safety Access Control Background. Digital Connect System With Integrated Circles, Flat Icons, Long Shadows. Network Interact Interface Concept. Cctv Vector Infographic Illustration
Vector, 0.5MB, 6135 × 6165 eps

Identity And Access Management Concept - IAM And IdAM - New Technologies To Ensure That The Right Users Within A Network Have Appropriate Access To Enterprise Resources - Users With IDs Within A Secure Perimeter - 3D Illustration
Image, 12.38MB, 9488 × 5298 jpg
Page 1 >> Next






















