Stock image Online Threat

Cyber Threat Intelligence Online Protection 3d Rendering Shows Online Malware Protection Against Ransomware Scams And Risks
Image, 2.93MB, 3740 × 3000 jpg

Bot Management Multi Color Concept Icon. Online Threat, Api. Web Application Security. Round Shape Line Illustration. Abstract Idea. Graphic Design. Easy To Use In Infographic, Presentation
Vector, 0.51MB, 5000 × 5000 eps

Types Of Application Security Solutions Rectangle Infographic Vector. Network Firewall. Data Visualization With 4 Steps. Editable Rectangular Options Chart. Lato-Bold, Regular Fonts Used
Vector, 1.2MB, 6000 × 3737 eps

Page Protection Blue Gradient Concept Icon. Network Security, Access Control. Service Availability. Round Shape Line Illustration. Abstract Idea. Graphic Design. Easy To Use In Infographic
Vector, 0.5MB, 5000 × 5000 eps

DDoS Mitigation Multi Color Concept Icon. Network Infrastructure, Web Traffic. Online Threat. Round Shape Line Illustration. Abstract Idea. Graphic Design. Easy To Use In Infographic, Presentation
Vector, 0.5MB, 5000 × 5000 eps

Discover Deceptive World Of Phishing Scams As Red Envelope Stands Out On Black Background. Cybercrime Concept. 3D Render Illustration.
Image, 4.26MB, 5500 × 3500 jpg

Software Security Solutions Types Circular Diagram Infographic. Network Firewall. Data Visualization With 4 Options. Hierarchy Chart Round. Montserrat SemiBold, Lato Regular Fonts Used
Vector, 1.22MB, 5000 × 5000 eps

Application Security Features Brochure Template. Leaflet Design With Linear Icons. Editable 4 Vector Layouts For Presentation, Annual Reports. Arial-Black, Myriad Pro-Regular Fonts Used
Vector, 1.93MB, 8000 × 2967 eps

DDoS Mitigation Blue Gradient Concept Icon. Network Infrastructure, Web Traffic. Online Threat. Round Shape Line Illustration. Abstract Idea. Graphic Design. Easy To Use In Infographic, Presentation
Vector, 0.52MB, 5000 × 5000 eps

Page Protection Multi Color Concept Icon. Network Security, Access Control. Service Availability. Round Shape Line Illustration. Abstract Idea. Graphic Design. Easy To Use In Infographic, Presentation
Vector, 0.49MB, 5000 × 5000 eps

Bot Management Blue Gradient Concept Icon. Online Threat, Api. Web Application Security. Round Shape Line Illustration. Abstract Idea. Graphic Design. Easy To Use In Infographic, Presentation
Vector, 0.52MB, 5000 × 5000 eps

Social Network Harassment, Criticism Or Bullying Concept. Aggressive Female Character Send Offensive Messages Online
Vector, 0.46MB, 5162 × 5000 eps
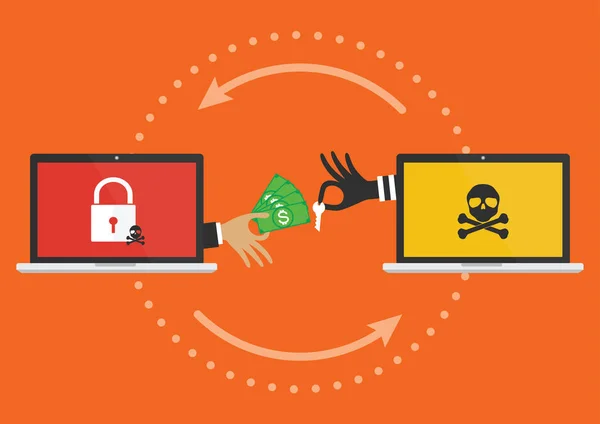
Businessman Hand Holding Money Banknote For Paying The Key From Hacker For Unlock Computer Folder Got Ransomware Malware Virus Computer PC. Vector Illustration Cybercrime Concept.
Vector, 2.51MB, 5661 × 4000 eps

Word VIRUS With Wooden Vintage Letters, A Laptop Keyboard Background.
Image, 13.91MB, 7360 × 4912 jpg

Cybersecurity As A Concept, Information Security And Encryption, Safe Access To User Personal Data, Safe Internet Access.
Image, 6.89MB, 6016 × 4016 jpg
Page 1 >> Next



































