Stock image Privacy Invasion

Problem Reaction Solution Text Message On Textured Grunge Copper And Vintage Gold Background
Image, 18.55MB, 5978 × 3985 jpg

Surveillance And Protection, This Security Camera Captures A Sense Of Vigilance And Control, Emphasizing The Importance Of Safety In Our Modern Society
Image, 10.31MB, 6521 × 4347 jpg

Mysterious Cyber Hacker With Obscured Face Standing Before A Screen With Futuristic Blue Digital Code Signifying Cybercrime And Security Breach
Image, 9.95MB, 6000 × 4000 jpg

Cyber Attack Privacy Invasion Text In Foreground Screen Of Code Editor Developer Studio Point Of Vue. Vulnerability Text In Attack System Ascii. Text In English, English Text
Image, 3.5MB, 7680 × 2160 jpg
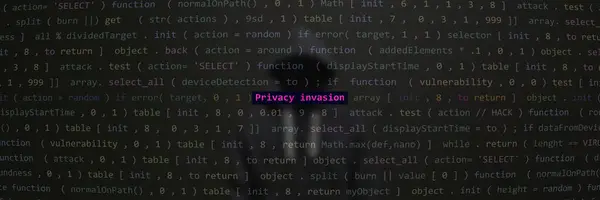
Cyber Attack Privacy Invasion Text In Foreground Screen, Anonymous Hacker Hidden With Hoodie In The Blurred Background. Vulnerability Text In Binary System Ascii Art Style, Code On Editor Screen. Text In English, English Text
Image, 4.96MB, 6480 × 2160 jpg

Nosey Neighbors Peek Though Their Window Blinds To See What You And Others In The Neighborhood Are Doing. This Is A 3-d Illustration.
Image, 1.72MB, 4500 × 5400 jpg

Cyber Attack Privacy Invasion Text In Foreground Screen, Hands Of A Anonymous Hacker On A Led Keyboard. Vulnerability Text In Informatic System Style, Code On Editor Screen. Text In English, English Text
Image, 4.43MB, 4608 × 3456 jpg

Cyber Attack Privacy Invasion Text In Foreground Screen, Hands Of A Anonymous Hacker On A Led Keyboard. Vulnerability Text In Informatic System Style, Code On Editor Screen.,English Language,text In English
Image, 1.73MB, 3840 × 2160 jpg

Secrets Unveiled: Woman Catches Man Hiding Smartphone Correspondence Leading To Family Conflict. High Quality 4k Footage
Image, 3.02MB, 3840 × 2160 jpg

Little Girl Keeping A Secret From Curious Friends Vector Cartoon Illustration. Funny Kids Eavesdropping Pressuring Their Friend To Drop Her Silence
Vector, 4.78MB, 8023 × 3676 eps

Cyber Attack Privacy Invasion Text In Foreground Screen Of Code Editor Developer Studio Point Of Vue. Vulnerability Text In Binary System Ascii. Text In English, English Text
Image, 2.54MB, 3840 × 2160 jpg

Stressed Woman Communicating Her Refusal Vector Cartoon Illustration
Vector, 4.87MB, 5740 × 3661 eps

An Anonymous Hooded Figure Stands Enshrouded In Digital Binary Code, Representing Cybersecurity And Hacking Concepts Against A Dark Backdrop
Image, 10.28MB, 8000 × 4000 jpg
Ethical Hacking Data Breach Tracking 2d Illustration Shows Corporate Tracking To Stop Technology Threats Vulnerability And Exploits
Image, 4.79MB, 3300 × 3000 jpg

Mobile Security Concept Vector Illustration With Multiple Secure And Unsecured Smart Phones
Vector, 1.24MB, 7016 × 4961 eps
Ethical Hacking Data Breach Tracking 2d Illustration Shows Corporate Tracking To Stop Technology Threats Vulnerability And Exploits
Image, 6.24MB, 3600 × 3000 jpg

Hacker Man In Black Using Computer Laptop For Criminal Activity Hacking Password And Private Information
Image, 3.33MB, 4472 × 3024 jpg

Certified Ethical Hacker Security Expert In Computer Penetration Consulting Company Education Paper Standard
Vector, 2.77MB, 7000 × 3000 eps

A Cybercriminal Breaching A Cell Phone's Security System To Gain Access To A User's Personal And Banking Data. Phishing Danger
Image, 7.26MB, 6016 × 4016 jpg
Ethical Hacker Tracking Server Vulnerability 3d Rendering Shows Testing Penetration Threats To Protect Against Attack Or Cybercrime
Image, 6.12MB, 3400 × 3000 jpg

Man In Black Holding Credit Card Using Computer Laptop For Criminal Activity Hacking Password And Private Information
Image, 4.59MB, 4225 × 2945 jpg

Hacker Man In Black Using Computer Laptop For Criminal Activity Hacking Password And Private Information
Image, 2.53MB, 4472 × 3039 jpg

Man In Black Holding Credit Card Using Computer Laptop For Criminal Activity Hacking Password And Private Information
Image, 3.02MB, 4592 × 3260 jpg

Man In Black Holding Credit Card And Lock Using Computer Laptop For Criminal Activity Hacking Bank Account Password
Image, 2.99MB, 3993 × 3051 jpg

Scammer Telephoning His Victims While Holding A Broken Padlock In His Hand Symbolizing Breached Security. Concept Of Vishing
Image, 5.01MB, 6016 × 4016 jpg

Hacker Man In Black Using Computer Laptop For Criminal Activity Hacking Password And Private Information
Image, 3.45MB, 4268 × 3129 jpg
Ethical Hacking Data Breach Tracking 3d Illustration Shows Corporate Tracking To Stop Technology Threats Vulnerability And Exploits
Image, 5.25MB, 4000 × 3000 jpg

Hacker Man In Black Using Computer Laptop For Criminal Activity Hacking Password And Private Information
Image, 2.63MB, 5312 × 3536 jpg

Man In Black Holding Credit Card And Lock Using Computer Laptop For Criminal Activity Hacking Bank Account Password
Image, 5.39MB, 3993 × 3051 jpg

Hacker Man In Black Using Computer Laptop For Criminal Activity Hacking Password And Private Information
Image, 2.59MB, 4268 × 3129 jpg

Vishing Scam. A Man Talks To A Hacker On The Phone While The Swindler Steals His Bank Details
Image, 8.58MB, 6961 × 4961 jpg

A Cybercriminal Breaking The Security System Of A Laptop To Scam Online. Danger And Phishing Alert. Hacker Scamming Through Web Pages
Image, 8.12MB, 6016 × 4016 jpg

Man In Black Holding Credit Card Using Computer Laptop For Criminal Activity Hacking Password And Private Information
Image, 3MB, 4409 × 3174 jpg

Man In Black Holding Credit Card Using Computer Laptop For Criminal Activity Hacking Password And Private Information
Image, 3.71MB, 4401 × 3070 jpg

Writing Note Showing Ethical Hacking. Business Concept For Act Of Locating Weaknesses And Vulnerabilities Of Computer
Image, 2.79MB, 4632 × 3092 jpg
Page 1 >> Next















