Stock image Security Compliance

Cropped View Of Businessman In Suit With Outstretched Hands And Gdpr Letters And Lock Illustration In Front
Image, 12.3MB, 7361 × 4913 jpg

Partial View Of Businessman Holding Digital Tablet With Lock Icon And Gdpr Letters Illustration Above On Blue Background
Image, 14.8MB, 7361 × 4913 jpg

Businessman In Suit Looking At Outstretched Hands With Internet Security Icon And Gbpr Letters Above Isolated On White
Image, 8.47MB, 4913 × 7388 jpg

Successful Businessman In Suit Pointing With Finger At Gdpr Compliant Illustration On White Background
Image, 10.24MB, 7361 × 4913 jpg
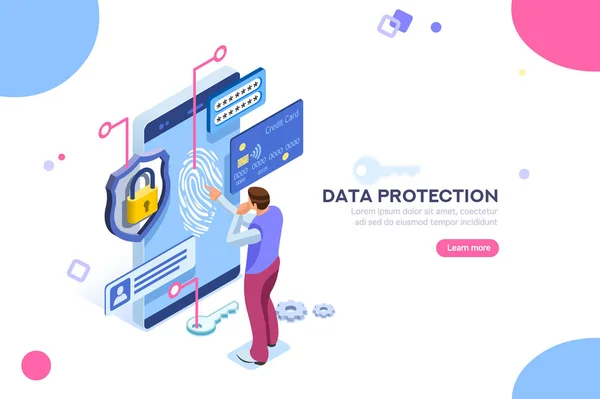
Data Protection Concept. Credit Card Check And Software Access Data As Confidential. Can Use For Web Banner, Infographics, Hero Images. Flat Isometric Illustration Isolated On White Background.
Vector, 1.69MB, 5000 × 3328 eps
Checkmarks Line Icons Set. Modern Graphic Design Concepts, Simple Outline Elements Collection. Vector Line Icons
Vector, 1.25MB, 5000 × 5000 eps

Compliance. Businessman's Hand Pressing The Icon With Text "compliance"
Image, 4.16MB, 7087 × 3456 jpg

Data Protection, Hosting Net Or Database Concept. Business Woman Applies Finger To Fingerprint Scanner To Access Database, Data Protection Concept
Vector, 10.22MB, 5000 × 5000 eps

Cloud Computing Security Business Metaphor In Blue Colors. Corporate Arm Reaching Out To A Lock Symbol Inside A Cloud Icon. The Padlock Repeats On Cellphone, Tablet PC And Laptop Within The Network.
Image, 0MB, 6048 × 4616 jpg

Network Security Antivirus Vpn Privacy. User Icon Vector. Data Protection. Data Secure. Icon For Concept Design. Isometric Vector. Personal Protection.
Vector, 4.62MB, 5904 × 4723 eps

Discover If Your Files Are Safe And Block Malicious Software Hidden Outside Of Files
Image, 1.99MB, 5100 × 3492 jpg

Trend Micro Endeavors To Develop And Release Products That Meet The Highest Standards Of Quality And Security
Image, 2.14MB, 5100 × 3492 jpg

Data Center Is A Facility That Houses Computing Resources, Such As Servers, Storage Systems, And Networking Equipment, Used To Process, Store, And Disseminate Data
Image, 1.98MB, 5100 × 3492 jpg

Kaspersky Security For Internet Gateway Is A Specialized Security Solution Designed To Protect Organizations' Internet Gateways From A Wide Range Of Cyber Threats
Image, 2.33MB, 4480 × 1993 jpg

Strategies For Integrating Continuous Improvement In Business Operations
Image, 10.3MB, 7212 × 4000 jpg

Allow Children To Explore The Web Safely, With Both Time And Content Limits
Image, 1.45MB, 5100 × 1733 jpg

Turns Any Public Hotspot Into A Secure WiFi Via VPN And Keeps Your Information Safe From Hackers
Image, 2.02MB, 5100 × 3492 jpg

Creating Effective Email Marketing Campaigns To Boost Customer Retention
Image, 10.62MB, 7212 × 4000 jpg

Trend Micro Is An Industry Leader In Antivirus Protection And Internet Security, With 30 Years Of Security Software Experience In Keeping Millions Of Users Safe
Image, 2.2MB, 5100 × 2550 jpg

Enjoy An Unlimited High-speed Connection With Full Anonymity. Access Just About Anything Online Quickly And Easily
Image, 2.07MB, 5100 × 3492 jpg

Business Security And Data Protection And Positive Mindset For Business Success Concept,
Vector, 5.13MB, 3000 × 3000 eps

Amazon Web Services (AWS) Is A Comprehensive And Widely Adopted Cloud Platform, Offering Over 200 Fully Featured Services From Data Centers Globally
Image, 2.08MB, 5100 × 3492 jpg

Kaspersky Security For Internet Gateway Is An Essential Tool For Organizations That Need To Secure Their Internet Access Points, Ensuring That Threats Are Detected And Blocked Before They Can Enter The Network
Image, 11.44MB, 7952 × 5304 jpg

Bank Online With Pay Guard To Ensure The Legitimacy Of Financial Sites
Image, 2.01MB, 5100 × 3492 jpg

Root Cause Analysis (RCA) Is A Powerful Problem-solving Tool That Helps Organizations Identify And Address The Underlying Causes Of Issues
Image, 10.74MB, 7212 × 4000 jpg

Relationship Between Root Cause Analysis And Corrective Action Plans
Image, 10.49MB, 7212 × 4000 jpg

Uses High-end Servers With No Speed, Traffic, Or Bandwidth Limitation
Image, 1.44MB, 5100 × 1733 jpg
Page 1 >> Next