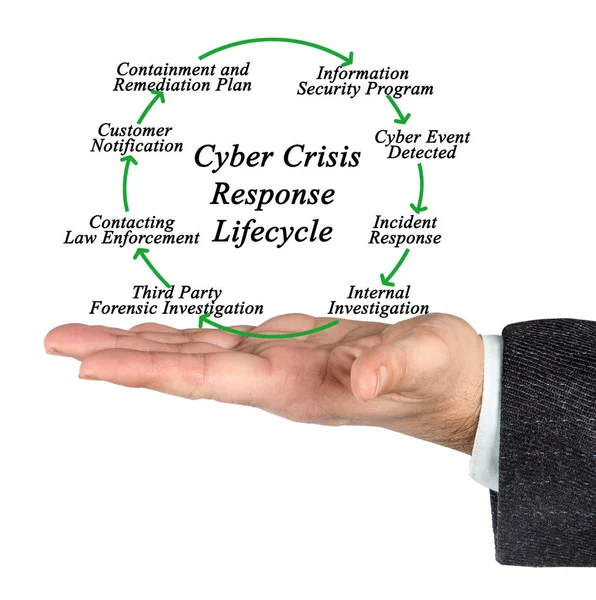
Stock image Security Incident Response

Incident Coordinator Pressing INCIDENT RESPONSE On An Interactive Touch Screen. Computer Security Concept. Man In Blue Suit Is Highlighting An Open Lock Among Forensic Tool Icons Signifying A Breach.
Image, 0MB, 7680 × 3840 jpg

Handwriting Text Computer Security Incident Response. Concept Meaning Technology Errors Safety Analysisagement Man In Business Suit Standing Pointing A Board With Bar Chart Copy Space.
Image, 1.79MB, 7000 × 7000 jpg

Word Writing Text Computer Security Incident Response. Business Concept For Technology Errors Safety Analysisagement Keyboard Key Intention To Create Computer Message, Pressing Keypad Idea.
Image, 3.67MB, 5616 × 3744 jpg

Emergency Cloud System Offers A Secure And Scalable Platform, Ensuring Continuous Data Access And Rapid Recovery During Crises
Image, 12.14MB, 7212 × 4000 jpg
Security Incident Duotone Line Icon , Vector, Pixel Perfect, Illustrator File
Vector, 0.34MB, 2400 × 1600 ai
Security Incident Color Shadow Thinline Icon , Vector, Pixel Perfect, Illustrator File
Vector, 0.34MB, 2400 × 1600 ai
Security Incident Color Circle Icon , Vector, Pixel Perfect, Illustrator File
Vector, 0.34MB, 2400 × 1600 ai

Emergency Cloud System Offers A Secure And Scalable Platform, Ensuring Continuous Data Access And Rapid Recovery During Crises
Image, 0.78MB, 6132 × 3000 jpg
Security Incident Thinline Icon , Vector, Pixel Perfect, Illustrator File
Vector, 0.34MB, 2400 × 1600 ai
Security Incident Lineal Color Icon , Vector, Pixel Perfect, Illustrator File
Vector, 0.35MB, 2400 × 1600 ai

Emergency Cloud System Offers A Secure And Scalable Platform, Ensuring Continuous Data Access And Rapid Recovery During Crises
Image, 12.86MB, 7212 × 4000 jpg
Security Incident Line Icon , Vector, Pixel Perfect, Illustrator File
Vector, 0.34MB, 2400 × 1600 ai

Handwriting Text Writing Incident Response. Concept Meaning Addressing And Analysisaging The Aftermath Of A Security Breach White Rectangle Clipboard With Blue Frame Has Two Holes Holds By Hands.
Image, 2.24MB, 7000 × 7000 jpg

Incident Coordinator Is Pressing INCIDENT RESPONSE On A Touch Screen Interface. Business Metaphor And Information Technology Concept For A Planned Reaction To A Security Breach Or Network Intrusion.
Image, 0MB, 7680 × 3840 jpg

Incident Response Written On Blue Key Of Metallic Keyboard. Finger Pressing Key
Image, 7.28MB, 5242 × 3744 jpg

Zero Trust - Zero Trust Network - Zero Trust Architecture - ZTA - Innovative Forms Of Cyber Security - Conceptual Illustration
Image, 11.8MB, 6500 × 3656 jpg

Writing Note Showing Incident Response. Business Concept For Addressing And Analysing The Aftermath Of A Security Breach
Image, 4.04MB, 6000 × 3614 jpg

Text Sign Showing Incident Management. Conceptual Photo Activities Of A Company To Identify And Correct Hazards Megaphone Extending The Capacity Of Volume Range Thru Blank Space Wide Beam.
Image, 1.52MB, 7000 × 4667 jpg

Security Manager Pressing CSIRT On A Screen. Technology Concept And Business Metaphor For Computer Security Incident Response Team. Several Icons Do Refer To Tasks Of Handling IT Security Incidents.
Image, 0MB, 7680 × 3840 jpg

Word Writing Text Incident Response. Business Photo Showcasing Addressing And Analysing The Aftermath Of A Security Breach Small Little Wallet Inside Man Trousers Front Pocket Near Notation Paper
Image, 14.83MB, 4005 × 6000 jpg

Handwriting Text Incident Response. Conceptual Photo Addressing And Analysing The Aftermath Of A Security Breach Note Paper Taped To Black Computer Screen Near Keyboard And Stationary
Image, 3.7MB, 4005 × 6000 jpg

Text Sign Showing Incident Management. Conceptual Photo Activities Of A Company To Identify And Correct Hazards.
Image, 3.34MB, 6000 × 3773 jpg

IT Director Is Touching COMPUTER SECURITY INCIDENT RESPONSE TEAM Onscreen. Security Technology And Business Concept For A Team Of Professional Cyber Firefighters Skilled To Counter Cybercrime..
Image, 0MB, 7680 × 3840 jpg

Man Is Pressing COMPUTER SECURITY INCIDENT MANAGEMENT On A Touch Screen Interface. Business Metaphor And Information Technology Concept For Monitoring Security Events On A Computer System Or Network.
Image, 0MB, 7680 × 3840 jpg

Conceptual Hand Writing Showing Computer Security Incident Management. Business Photo Showcasing Safe Cyber Technology Analysisaging Man Holding Above His Head Blank Rectangular Colored Board.
Image, 2.03MB, 7000 × 6969 jpg

NCSD National Cyber Security Division Written On Green Key Of Metallic Keyboard. Finger Pressing Key.
Image, 7.63MB, 5242 × 3744 jpg

Incident Management Process Business Technology Concept, Business Person Hand Holding Incident Management Icon On Virtual Screen.
Image, 7.36MB, 6000 × 4000 jpg

Incident Response - 3D Rendering Metal Word On White Background - Concept Illustration
Image, 2.16MB, 5000 × 2500 jpg

Incident Response - Organized Approach To Addressing And Managing The Aftermath Of A Security Breach Or Cyberattack, Text Concept Background
Vector, 35.17MB, 16667 × 6252 eps
Incident Management Banner With Icons. Incident, Alert, Investigation, Analysis, Identify, Regulations, Restore, Report Icons. Business Concept. Web Vector Infographic In 3D Style
Vector, 3.29MB, 9001 × 2701 eps

Phishing Email, Cyber Criminals, Hackers, Phishing Email To Steal Personal Data, Hacked Laptop, Malware, Infected Email, Scene Of A Person Working On A Laptop With An Infected Email On The Screen
Vector, 0.4MB, 10942 × 6022 ai
Page 1 >> Next