Stock image Spoofing

Word Writing Text Spoofing Attack. Business Photo Showcasing Impersonation Of A User, Device Or Client On The Internet
Image, 2.28MB, 5955 × 3350 jpg

Businessman Taking A Credit Card From A User's Smartphone, Cybersecurity And Phishing Concept
Image, 12.17MB, 6002 × 4001 jpg

Handwriting Text Spoofing Attack. Concept Meaning Impersonation Of A User, Device Or Client On The Internet Megaphones Drawing Giving Positive Comments Making Announcement
Image, 2.51MB, 8000 × 8000 jpg

Tiny Hacker Character Hacking Credit Card, Steal Personal Data From Laptop Screen. Phishing Via Internet, Email Spoofing
Vector, 0.4MB, 6760 × 5000 eps

Tiny Hackers Male Characters Sitting On Huge Computer With Rods Phishing Via Internet, Email Spoofing, Fishing Messages
Vector, 0.99MB, 5530 × 4000 eps

Cyber Security Concept Illustration In 3d Design. Phishing Scam, Hacker Attack Of Bank Account, Online Fraud, Scam And Steal. Hacking Credit Card Isometric Design Of Illustration.
Vector, 3.22MB, 5000 × 5001 eps
Hacker Phishing Banner. Isometric Illustration Of Hacker Phishing Vector Banner For Web Design
Vector, 1.35MB, 6000 × 3000 eps

Tiny Hacker Male Character Sitting On Huge Computer With Rod Phishing And Hacking Files, Personal Data, Credentials Via Internet. Email Spoofing Or Fishing Messages. Cartoon People Vector Illustration
Vector, 0.3MB, 5471 × 5000 eps

Digital Personality Vector Illustration. Fake Feelings Tiny Persons Concept
Vector, 0.73MB, 6000 × 3140 eps

Phishing Email, Cyber Criminals, Hackers, Phishing Email To Steal Personal Data, Hacked Laptop, Malware, Infected Email, Scene Of A Person Working On A Laptop With An Infected Email On The Screen
Vector, 0.4MB, 10942 × 6022 ai

Hacker Attack, Mobile Security Concept, Data Protection, Cyber Crime, 3d Isometric Vector Illustration, Fingerprint, Phishing Scam, Information Protection, Smartphone Safety
Vector, 2.26MB, 6251 × 4497 eps

Flag Of Switzerland On A Computer Binary Codes Falling From The Top And Fading Away.
Image, 17.78MB, 6010 × 5999 jpg

Flag Of Zimbabwe On A Computer Binary Codes Falling From The Top And Fading Away.
Image, 18.51MB, 9000 × 4520 jpg

Cyber Attack Email Spoofing Text In Foreground Screen Of Code Editor Developer Studio Point Of Vue. Vulnerability Text In Attack System Ascii. Text In English, English Text
Image, 3.61MB, 7680 × 2160 jpg

Cyber Deception Is A Technique Used To Consistently Trick An Adversary During A Cyber-attack, Text Concept On Notepad
Image, 7.77MB, 5760 × 3840 jpg

Spoofing Attack Cyber Crime Hoax 2d Illustration Means Website Spoof Threat On Vulnerable Deception Sites
Image, 6.77MB, 4000 × 3000 jpg

Backscatter Written On Blue Key Of Metallic Keyboard. Finger Pressing Key.
Image, 7.24MB, 5242 × 3744 jpg

Firewall Attack, Phishing Scam, Data Theft, Hackers Breaking Wall To Steal Data, Information Protection Concept, Cyber Crime, Computer Safety And Security, 3d Isometric Illustration
Vector, 2.36MB, 4622 × 4000 eps

Phishing, Cybercrime Concept - Infographics Or Mind Map In A Notebook
Image, 15.58MB, 5600 × 4000 jpg

Computer Monitor With Files And Personal Data Hang On Hooks At Screen. Phishing, Hacker Attack, Lose Money In Internet, Scam Email Letters, Fraud Activity, Carding Concept. Cartoon Vector Illustration
Vector, 0.32MB, 8869 × 5000 eps

Set Of Stickers Hacker Attack, Phishing, Stealing Personal Data, Spoofing In Internet. Cyber Security Concept. Bulgar Characters Steal Data Online. Computer, Key, Lock, Shield. Cartoon Vector Patches
Vector, 0.52MB, 9307 × 5000 eps

Flag Of Tanzania On A Computer Binary Codes Falling From The Top And Fading Away.
Image, 22.58MB, 9000 × 6000 jpg

Flag Of Spain On A Computer Binary Codes Falling From The Top And Fading Away.
Image, 28.37MB, 9000 × 6000 jpg

Flag Of Portugal On A Computer Binary Codes Falling From The Top And Fading Away.
Image, 26.88MB, 9000 × 6000 jpg

DKIM _ DomainKeys Identified Mail, Letters And Icons, And Vector Illustration.
Vector, 1.24MB, 4319 × 3402 eps

20 Euro Bills And Smartphone With Police Handcuffs. Concept Of Hackers Phishing Attacks, Illegal Scam Or Online Spyware Soft Distribution
Image, 3.75MB, 4928 × 3264 jpg

Phishing-1 Detailed Circular Flat Vector Icon. Vector Isolated Concept Metaphor Illustrations.
Vector, 2.59MB, 6945 × 6945 eps

Email Spoofing Written On Blue Key Of Metallic Keyboard. Finger Pressing Key.
Image, 7.29MB, 5242 × 3744 jpg
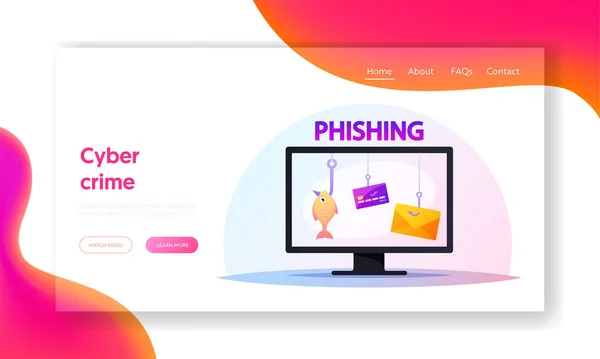
Scam, Fraud Activity Landing Page Template. Computer Monitor With Credit Cards Hanging On Hooks, Victims Of Phishing
Vector, 2.94MB, 6668 × 4000 eps

Flag Of Ukraine On A Computer Binary Codes Falling From The Top And Fading Away.
Image, 28.61MB, 9000 × 6000 jpg

Phishing And Cyber Security: Hacker Stealing A User's Credit Card Information On A Smartphone
Image, 9.91MB, 6000 × 4000 jpg

Vector Illustration Of Hacker Penetrating A Hand Shake Of Two Mobile Phone. Cybersecurity Concept. Unsecure Connection.
Vector, 15.6MB, 6500 × 3500 eps

Phishing Via Internet Concept. Email Spoofing Or Fishing Messages. Hacking Credit Card Or Personal Id Information Website. Cyber Banking Account Attack Online Security. Eps 10 Vector Illustration Flat
Vector, 6.28MB, 6000 × 4000 eps
Page 1 >> Next