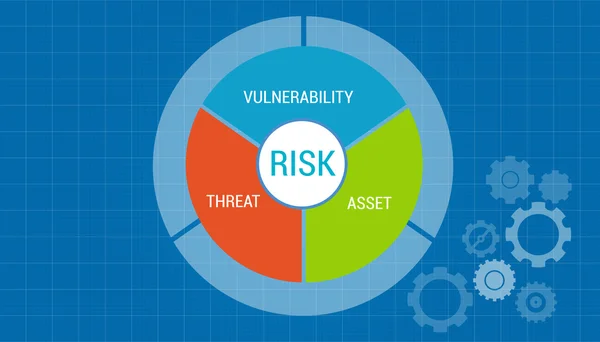
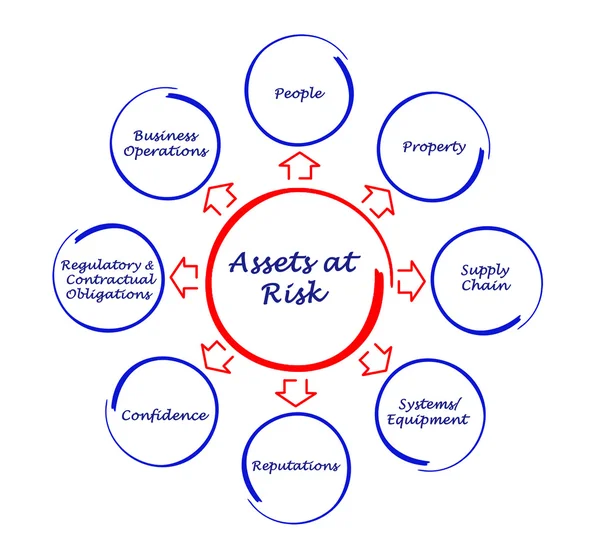
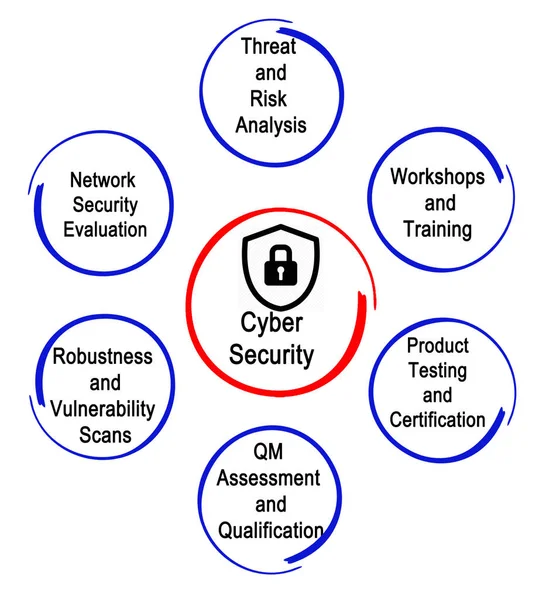
Stock image Vulnerability Assessment

Cropped View Of Computer Systems Analysts Working With Charts At Table
Image, 14.47MB, 7360 × 4912 jpg

Selective Focus Of Data Analyst Pointing With Hand On Computer Monitor To Colleague In Office
Image, 18.16MB, 7360 × 4912 jpg

Word Writing Text Security Assessment. Business Concept For Study To Locate IT Security Vulnerabilities And Risks.
Image, 4.43MB, 6000 × 4005 jpg

Cropped View Of Information Security Analyst Pointing With Finger On Charts On Computer Monitor, Panoramic Shot
Image, 8.53MB, 7360 × 2284 jpg

Text Sign Showing Security Assessment. Conceptual Photo Study To Locate IT Security Vulnerabilities And Risks.
Image, 2.13MB, 4533 × 2763 jpg

Selective Focus Of Papers With Graphs On Table And Data Analyst Working In Office
Image, 13.27MB, 4912 × 7360 jpg

Text Sign Showing Vulnerability. Conceptual Photo State Of Being Exposed To The Possibility Of Being Attacked Elements Of This Image Furnished By NASA.
Image, 3.84MB, 6000 × 4005 jpg
Cropped View Of Computer Systems Analyst Pointing With Finger At Graphs On Computer Monitor, Panoramic Shot
Image, 7.77MB, 6669 × 2070 jpg

Text Sign Showing Security Assessment. Conceptual Photo Study To Locate IT Security Vulnerabilities And Risks.
Image, 4.15MB, 6000 × 4005 jpg

Selective Focus Of Data Analyst Using Digital Tablet Near Colleague At Table With Computers
Image, 10.78MB, 7360 × 4912 jpg

Selective Focus Of Information Security Analysts Working With Computers And Papers At Table In Office
Image, 12.83MB, 7360 × 4912 jpg

Side View Of Information Security Analyst Looking At Charts Near Graphs On Computer Monitors In Office
Image, 14.6MB, 7360 × 4912 jpg
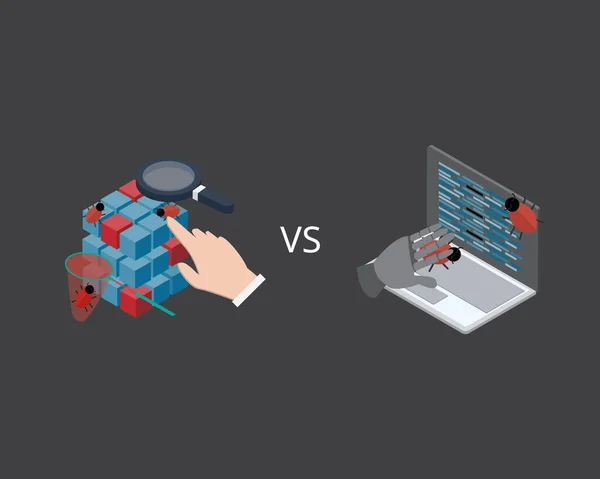
Manual Tester And Automated Software Tester Bug To Do QA Testing To Test Software
Vector, 5.86MB, 5000 × 4000 eps

Side View Of Information Security Analysts Using Charts While Testing Security Of Computer Systems
Image, 11.31MB, 7360 × 4912 jpg

Penetration Testing Or Pen Test To Analyze A Potential Cyber Attack And Its Potential Vulnerabilities For Database
Vector, 5.76MB, 5000 × 4000 eps

Cropped View Of Data Analyst Showing Thumb Up Gesture To Colleague With Coffee To Go
Image, 13.2MB, 7360 × 4912 jpg

Bug Bounty Program Is A Deal Offered For Hackers Or Developers To Receive Compensation For Reporting Bugs, Security Exploits And Vulnerabilities
Vector, 5.91MB, 5000 × 4000 eps

Cropped View Of Information Security Analyst Planning Strategy With Charts At Table
Image, 13.86MB, 7360 × 4912 jpg

Bug Bounty Program Is An Offer For Hackers Or Developers To Receive Compensation For Reporting Bugs, Security Exploits And Vulnerabilities
Vector, 5.77MB, 5000 × 4000 eps

Selective Focus Of Data Analyst Looking At Charts On Paper While Working With Colleague In Office
Image, 15.9MB, 7360 × 4912 jpg

Bug Bounty Program Is An Offer For Hackers Or Developers To Receive Compensation For Reporting Bugs, Security Exploits And Vulnerabilities
Vector, 5.74MB, 5000 × 4000 eps

Cropped View Of Data Analyst Pointing With Finger At Charts Near Computer On Table
Image, 11.38MB, 7360 × 4912 jpg

Continuous Monitoring Of Cloud Environments Detects And Responds To Security Incidents In Real-time, Mitigating Potential Threats
Image, 1.13MB, 6132 × 3000 jpg

Side View Of Data Analyst Pointing With Hand At Graphs On Computer Monitor To Colleague In Office
Image, 12.51MB, 4728 × 7084 jpg

Obust Access Control Mechanisms Enforce Least Privilege Principles, Limiting Access To Data And Resources Based On User Roles And Permissions
Image, 10.95MB, 7212 × 4000 jpg
Selective Focus Of Data Analyst Looking At Colleague Holding Papers With Graphs In Office
Image, 17.01MB, 4912 × 7360 jpg

Cropped View Of Data Analyst Holding Papers With Graphs Near Colleague Showing Dubium Gesture At Table
Image, 11.91MB, 7360 × 4912 jpg

Selective Focus Of Computer Systems Analysts Using Smartphone And Graphs While Working In Office
Image, 17.04MB, 4912 × 7360 jpg

Types Of Penetration Testing Onboarding Mobile App Screen. Walkthrough 3 Steps Editable Graphic Instructions With Linear Concepts. UI, UX, GUI Template. Montserrat SemiBold, Regular Fonts Used
Vector, 1.13MB, 6000 × 3978 eps
Back View Of Data Analyst Pointing On Charts On Computer Monitor Near Laptop With Blank Screen On Table
Image, 15.53MB, 7360 × 4912 jpg

Kaspersky Vulnerability And Patch Management Is A Comprehensive Solution Designed To Help Organizations Identify And Address Security Vulnerabilities In Their IT Infrastructure
Image, 1.1MB, 2600 × 1728 jpg
Selective Focus Of Data Analysts Working With Graphs On Computer Monitors In Office, Panoramic Shot
Image, 7.24MB, 7360 × 2284 jpg

Gray Box Blue Gradient Concept Icon. Data Protection. Information Security, Vulnerability. Round Shape Line Illustration. Abstract Idea. Graphic Design. Easy To Use In Infographic, Presentation
Vector, 0.51MB, 5000 × 5000 eps

Selective Focus Of Data Analyst Pointing On Chart To Colleague In Office
Image, 17.32MB, 7360 × 4912 jpg

Cropped View Of Data Analyst Holding Paper Cup And Talking To Colleague
Image, 15.51MB, 7360 × 4912 jpg

Penetration Testing Stages To Better Understand How A Potential Cyber Attack And Its Potential Vulnerabilities For Security
Vector, 5.93MB, 5000 × 4000 eps
Page 1 >> Next