Stock image Endpoint

Manager Is Pushing ENDPOINT SECURITY On A Virtual Touch Screen Interface. Information Technology And Security Concept For Software And Technology Protecting Corporate Computing Networks.
Image, 0MB, 7680 × 3840 jpg

Cloud Computing And Networks Concept With Laptop Computer And Smart Phone
Vector, 2.1MB, 5000 × 5000 eps

Cloud Computing Concept - Connected Digital Global Networks - Black And White EPS10 Vector For Your Business
Vector, 2.34MB, 5000 × 5000 eps

Cloud Computing And Networks Concept With Laptop Computer And Smart Phone
Vector, 4.91MB, 5000 × 5000 eps

Phishing Email, Cyber Criminals, Hackers, Phishing Email To Steal Personal Data, Hacked Laptop, Malware, Infected Email, Scene Of A Person Working On A Laptop With An Infected Email On The Screen
Vector, 0.4MB, 10942 × 6022 ai

Data Security Concept - Practice Of Protecting Digital Information From Unauthorized Access Throughout Its Lifecycle - 3D Illustration
Image, 8.84MB, 8432 × 4882 jpg

Communication Technology , Smart Connection IOT And People Network Technology Concept. People Using Connective Device To Connect To The Secured Internet Network And Cloud Computing Server Vexel
Image, 10.53MB, 7587 × 3000 jpg

Cyber Attack Endpoint Protection Text In Foreground Screen, Anonymous Hacker Hidden With Hoodie In The Blurred Background. Vulnerability Text In Binary System Ascii Art Style, Code On Editor Screen. Text In English, English Text
Image, 5.04MB, 6480 × 2160 jpg

Close-up Of Smiling Woman's Face Looking At The Peak Of A Large Snowy Mountain Reflected In Her Round Sunglasses
Image, 16.14MB, 6555 × 4370 jpg

Communication Technology , Smart Connection IOT And People Network Technology Concept. People Using Connective Device To Connect To The Secured Internet Network And Cloud Computing Server Kudos
Image, 4.76MB, 5000 × 2500 jpg
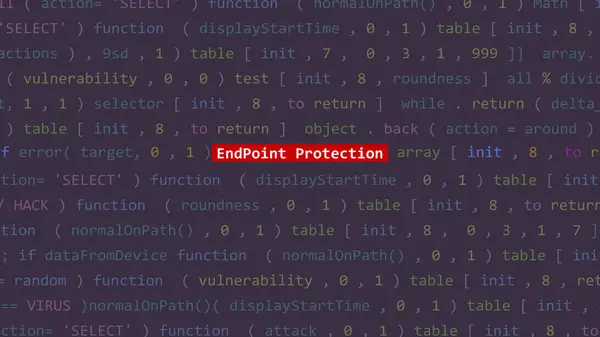
Cyber Attack Endpoint Protection Text In Foreground Screen Of Code Editor Developer Studio Point Of Vue. Vulnerability Text In Binary System Ascii. Text In English, English Text
Image, 2.5MB, 3840 × 2160 jpg

Cyber Attack Endpoint Detection Text In Foreground Screen Of Code Editor Developer Studio Point Of Vue. Vulnerability Text In Attack System Ascii. Text In English, English Text
Image, 3.8MB, 7680 × 2160 jpg

VPI _ Virtual Path Identifier, Letters And Icons, And Vector Illustration.
Vector, 1.24MB, 3402 × 3402 eps

Communication Technology , Smart Connection IOT And People Network Technology Concept. People Using Connective Device To Connect To The Secured Internet Network And Cloud Computing Server Kudos
Image, 5.5MB, 6250 × 2500 jpg

Container Security Concept - App Security - Practice Of Protecting Containerized Applications From Potential Risks - 3D Illustration
Image, 10.24MB, 9584 × 5298 jpg

Dhaka, Bangladesh- 09 Aug 2024: Trend Micro Inc. Logo Is Displayed On Smartphone. Trend Micro Inc.is An American Japanesecyber Securitysoftware Company.
Image, 9.6MB, 6000 × 4000 jpg

Discover If Your Files Are Safe And Block Malicious Software Hidden Outside Of Files
Image, 1.99MB, 5100 × 3492 jpg

Trend Micro Endeavors To Develop And Release Products That Meet The Highest Standards Of Quality And Security
Image, 2.14MB, 5100 × 3492 jpg

Data Center Is A Facility That Houses Computing Resources, Such As Servers, Storage Systems, And Networking Equipment, Used To Process, Store, And Disseminate Data
Image, 1.98MB, 5100 × 3492 jpg

Communication Technology , Smart Connection IOT And People Network Technology Concept. People Using Connective Device To Connect To The Secured Internet Network And Cloud Computing Server Vexel
Image, 9.68MB, 7193 × 3000 jpg

Communication Technology , Smart Connection IOT And People Network Technology Concept. People Using Connective Device To Connect To The Secured Internet Network And Cloud Computing Server Vexel
Image, 13.83MB, 9333 × 3472 jpg

Communication Technology , Smart Connection IOT And People Network Technology Concept. People Using Connective Device To Connect To The Secured Internet Network And Cloud Computing Server Vexel
Image, 14.63MB, 9237 × 3305 jpg

Office 365 Migration Involves Transitioning An Organization's Existing Email, Documents, And Collaboration Systems To The Microsoft 365 Cloud Environment
Image, 3.2MB, 5100 × 3492 jpg
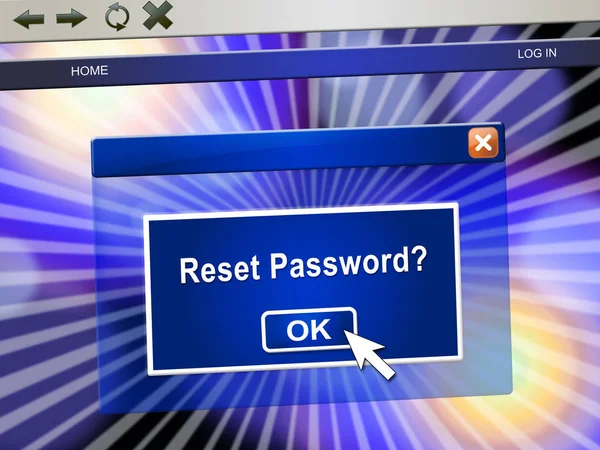
Reset Password Popup To Redo Security Of PC. New Code For Securing Computer - 3d Illustration
Image, 8.2MB, 4000 × 3000 jpg

Conceptual Hand Writing Showing Endpoint Security. Concept Meaning The Methodology Of Protecting The Corporate Network
Image, 3.86MB, 6000 × 4005 jpg

Cloud Services Concept. Bright Cloud Logo Made From Cables And Connected To The Cloud Switch Port And Endpoints. Closeup.
Image, 1.86MB, 5616 × 3744 jpg

UEM Unified Endpoint Management Written On Green Key Of Metallic Keyboard. Finger Pressing Key.
Image, 7.63MB, 5242 × 3744 jpg
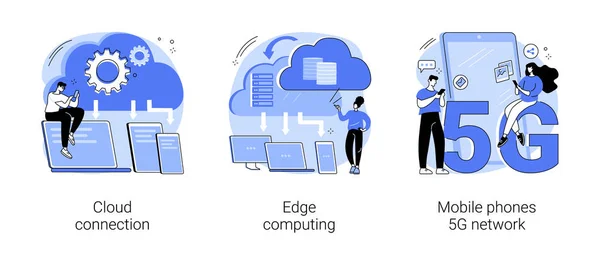
Online Data Transfer Abstract Concept Vector Illustration Set. Cloud Connection, Edge Computing, Mobile Phones 5G Network, Database Connection, Local Data Storage, 5G Technology Abstract Metaphor.
Vector, 5.47MB, 7293 × 3126 eps

Endpoint Security Safe System Shows Safeguard Against Virtual Internet Threat - 2d Illustration
Image, 6.45MB, 3600 × 3000 jpg

Behavioral Biometrics Concept - Security Technology That Identifies Individuals Based On Unique Patterns In Their Activities And Behaviors To Authenticate And Monitor Them - 3D Illustration
Image, 12.78MB, 9584 × 5298 jpg

Host-based Intrusion Detection Systems Concept - HIDS - Technologies That Monitor And Analyze The Internals Of A Computing System To Detect Potential Threats - 3D Illustration
Image, 12.39MB, 9584 × 5298 jpg
Page 1 >> Next