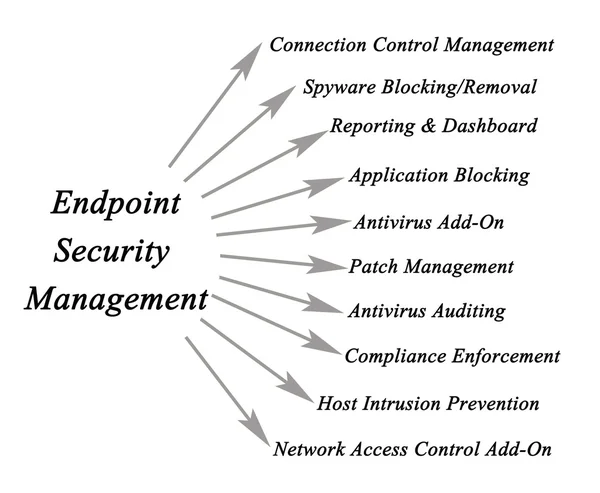
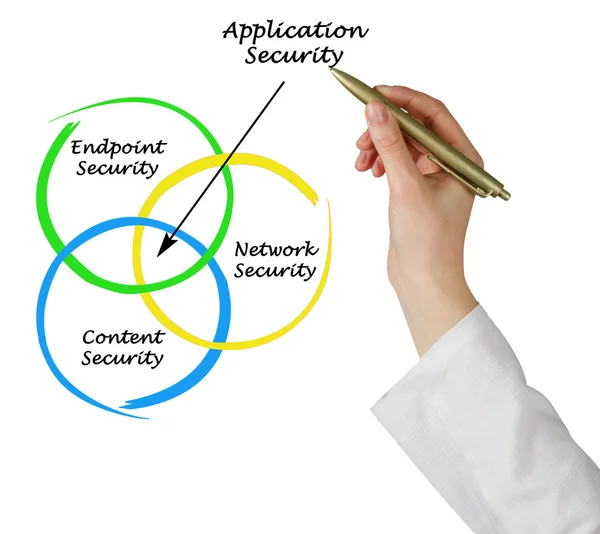
Stock image Endpoint page 2

Implement SSO Solutions To Enable Users To Log In Once And Gain Access To Multiple Financial Services Without Needing To Re-authenticate
Image, 0.8MB, 2600 × 1728 jpg

Discover If Your Files Are Safe And Block Malicious Software Hidden Outside Of Files
Image, 1.99MB, 5100 × 3492 jpg

Trend Micro Endeavors To Develop And Release Products That Meet The Highest Standards Of Quality And Security
Image, 2.14MB, 5100 × 3492 jpg

Data Center Is A Facility That Houses Computing Resources, Such As Servers, Storage Systems, And Networking Equipment, Used To Process, Store, And Disseminate Data
Image, 1.98MB, 5100 × 3492 jpg

Communication Technology , Smart Connection IOT And People Network Technology Concept. People Using Connective Device To Connect To The Secured Internet Network And Cloud Computing Server Vexel
Image, 9.68MB, 7193 × 3000 jpg

Communication Technology , Smart Connection IOT And People Network Technology Concept. People Using Connective Device To Connect To The Secured Internet Network And Cloud Computing Server Vexel
Image, 13.83MB, 9333 × 3472 jpg

Communication Technology , Smart Connection IOT And People Network Technology Concept. People Using Connective Device To Connect To The Secured Internet Network And Cloud Computing Server Vexel
Image, 14.63MB, 9237 × 3305 jpg

Office 365 Migration Involves Transitioning An Organization's Existing Email, Documents, And Collaboration Systems To The Microsoft 365 Cloud Environment
Image, 3.2MB, 5100 × 3492 jpg

A Jigsaw Puzzle With A Piece Missing And The Word Endpoint Security Written In The Gap. The Puzzle Is On A Blue Background
Image, 11.13MB, 5489 × 3214 jpg

Paper Page With Curly Corners. Vector Document Rolled Borders, Realistic 3d Sheet Bent Angle Or Bookmarks With Creased Angles. Isolated Leaf Of Magazine, Sticker Curved Endpoints Edges Set
Vector, 2.8MB, 7950 × 2382 eps

Communication Technology , Smart Connection IOT And People Network Technology Concept. People Using Connective Device To Connect To The Secured Internet Network And Cloud Computing Server Vexel
Image, 11.17MB, 9237 × 3305 jpg
Reset Password Popup To Redo Security Of PC. New Code For Securing Computer - 3d Illustration
Image, 8.2MB, 4000 × 3000 jpg

Conceptual Hand Writing Showing Endpoint Security. Concept Meaning The Methodology Of Protecting The Corporate Network
Image, 3.86MB, 6000 × 4005 jpg

Cloud Services Concept. Bright Cloud Logo Made From Cables And Connected To The Cloud Switch Port And Endpoints. Closeup.
Image, 1.86MB, 5616 × 3744 jpg

UEM Unified Endpoint Management Written On Green Key Of Metallic Keyboard. Finger Pressing Key.
Image, 7.63MB, 5242 × 3744 jpg
Online Data Transfer Abstract Concept Vector Illustration Set. Cloud Connection, Edge Computing, Mobile Phones 5G Network, Database Connection, Local Data Storage, 5G Technology Abstract Metaphor.
Vector, 5.47MB, 7293 × 3126 eps

Endpoint Security Safe System Shows Safeguard Against Virtual Internet Threat - 2d Illustration
Image, 6.45MB, 3600 × 3000 jpg

Behavioral Biometrics Concept - Security Technology That Identifies Individuals Based On Unique Patterns In Their Activities And Behaviors To Authenticate And Monitor Them - 3D Illustration
Image, 12.78MB, 9584 × 5298 jpg

Host-based Intrusion Detection Systems Concept - HIDS - Technologies That Monitor And Analyze The Internals Of A Computing System To Detect Potential Threats - 3D Illustration
Image, 12.39MB, 9584 × 5298 jpg

STUTTGART, GERMANY - Mar 09, 2021: Mobile Phone With Logo Of Cyber Security Company CrowdStrike Holdings Inc. On Screen In Front Of Web Page. Focus On Center-left Of Phone Display.
Image, 6.14MB, 4500 × 3376 jpg

Zero Trust - Zero Trust Network - Zero Trust Architecture - ZTA - Innovative Forms Of Cyber Security - Conceptual Illustration
Image, 11.8MB, 6500 × 3656 jpg

Cyber Attack Endpoint Detection Text In Foreground Screen, Anonymous Hacker Hidden With Hoodie In The Blurred Background. Vulnerability Text In Binary System Ascii Art Style, Code On Editor Screen. Text In English, English Text
Image, 4.97MB, 6480 × 2160 jpg

Geographical Proximity To Users Can Impact Latency And Response Times
Image, 10.92MB, 7212 × 4000 jpg

Regional Cloud Availability Enables Businesses To Adhere To Local Compliance Requirements
Image, 0.94MB, 6132 × 3000 jpg

Compliance Settings Help Organizations Meet Industry Standards And Regulatory Requirements
Image, 9.71MB, 7212 × 4000 jpg

Continuous Monitoring Of Cloud Environments Detects And Responds To Security Incidents In Real-time, Mitigating Potential Threats
Image, 1.13MB, 6132 × 3000 jpg

Obust Access Control Mechanisms Enforce Least Privilege Principles, Limiting Access To Data And Resources Based On User Roles And Permissions
Image, 10.95MB, 7212 × 4000 jpg

Strategies For Integrating Continuous Improvement In Business Operations
Image, 10.3MB, 7212 × 4000 jpg

API Integration - Application Programming Interface Connects Software Applications To Enable Data Exchange And Functionality Sharing. API Automation, Programming, System Integration Illustration.
Vector, 5.61MB, 5000 × 3800 eps

Communication Technology , Smart Connection IOT And People Network Technology Concept. People Using Connective Device To Connect To The Secured Internet Network And Cloud Computing Server Kudos
Image, 6.83MB, 7498 × 2500 jpg

Communication Technology , Smart Connection IOT And People Network Technology Concept. People Using Connective Device To Connect To The Secured Internet Network And Cloud Computing Server Vexel
Image, 9.66MB, 8603 × 3300 jpg

Communication Technology , Smart Connection IOT And People Network Technology Concept. People Using Connective Device To Connect To The Secured Internet Network And Cloud Computing Server Kudos
Image, 6.01MB, 6250 × 2500 jpg

Turns Any Public Hotspot Into A Secure WiFi Via VPN And Keeps Your Information Safe From Hackers
Image, 2.02MB, 5100 × 3492 jpg
Previous << Page 2 >> Next